I began writing for The Washington Post in 1996, and started covering computer and Internet security in 1999. Below are links to what I believe is some of my best work over the past four years or so. Virtually all of the stories and blog posts listed here were either Washington Post/Security Fix exclusives, or were the result of my investigative reporting and research aimed at shining a light on the Internet’s darkest corners, and educating readers about the importance of security.
Series: Cyber Gangs Fleece Small Businesses
Louisiana Firm Sues Capital One After Losing Thousands in Online Bank Fraud Dec. 7, 2009 — An electronics testing firm in Louisiana is suing its bank, Capital One, alleging that the financial institution was negligent when it failed to stop hackers from transferring nearly $100,000 out of its account earlier this year. In August, Security Fix wrote about the plight of Baton Rouge-based JM Test Systems, an electronics testing firm that in February lost more than $97,000 from two separate unauthorized bank transfers a week apart.
D.C. Businessman Loses Thousands After Clicking Wrong E-mail Dec. 1, 2009 — The latest victim to learn this was Nigel Parkinson, president of D.C.-based Parkinson Construction, a firm with an estimated $20 million in annual revenue that has worked on some of Washington’s top gathering places, including the new D.C. Convention Center and the Nationals baseball stadium.
Hackers Attempt to Take $1.3 Million from D.C Firm Nov. 30, 2009 — Most of the fraud against small businesses that I have been chronicling succeeded because the fraudsters were able to steal the victim’s online banking credentials and initiate a series of bogus payroll payments directly to so-called money mules, accomplices hired through work-at-home job schemes who are instructed to withdraw the money and wire it overseas (typically minus an eight percent commission). But according to this woman’s bank, the attackers set the unauthorized transfers in motion by using another company’s compromised account to initiate a “pull” or withdrawal from her company’s bank account. The crooks instructed nearly $1 million to be transferred from the D.C. firm to a company in West Virginia, and about $100,000 was sent to a company in Manteno, Ill. called Bill Anderson Painting.
Business E-Banking and the 6-Figure Password Nov. 4, 2009 — On Monday, Security Fix featured the story of Ronnie Cutshall, a Tennessee man who was caught up in an international money laundering scam after being recruited through a work-at-home job offer. That story mentioned that Cutshall received a $9,600 transfer from a company called American Realty, but that I didn’t have any luck in tracking down the victim company. Today the American Realty company affected by that scam contacted me after reading my story (turns out they’re located in Shalimar, Fla., not Georgia, as I had previously thought).
FDIC: Uptick in ‘Money Mule’ Scams Nov. 2, 2009 — The Federal Deposit Insurance Corporation (FDIC) is warning financial institutions about an uptick in scams involving unauthorized funds transfers from hacked online bank accounts to so-called “money mules,” people hired through work-at-home scams to help cyber criminals overseas launder money.
 FBI: Cyber Crooks Stole $40M from U.S. Small, Mid-Sized Firms Oct. 26, 2009 — Cyber criminals have stolen at least $40 million from small to mid-sized companies across America in a sophisticated but increasingly common form of online banking fraud, the FBI said this week.
FBI: Cyber Crooks Stole $40M from U.S. Small, Mid-Sized Firms Oct. 26, 2009 — Cyber criminals have stolen at least $40 million from small to mid-sized companies across America in a sophisticated but increasingly common form of online banking fraud, the FBI said this week.
E-Banking on a Locked Down PC Oct. 20, 2009 — From where I sit, any solution that fails to assume that a customer’s system is already completely owned by the bad guys doesn’t have a prayer of outsmarting today’s threats. I find it strange that so few security companies are talking about what appears to be a clear demand for better back-end fraud detection technologies by many of the nation’s banks (more on this topic in a future column).
Avoid Windows Malware: Bank on a Live CD Oct. 12, 2009 — An investigative series I’ve been writing about organized cyber crime gangs stealing millions of dollars from small to mid-sized businesses has generated more than a few responses from business owners who were concerned about how best to protect themselves from this type of fraud. The simplest, most cost-effective answer I know of? Don’t use Microsoft Windows when accessing your bank account online. 
Trojan Turns Smash & Grab into Grab & Smash Oct. 14, 2009 — Imagine being in charge of your organization’s finances, and learning from your bank one morning that thieves had stolen tens of thousands of dollars from company coffers overnight using your online banking credentials. Now imagine your frustration when you go to log in to your PC to assess the damage, only to find that the computer you typically use to access the account has been kneecapped by the bad guys. This is precisely what happened to Kathy Dake, office manager for St. Isidore Catholic Church in Danville, Calif. Dake had infected her PC with the Zeus Trojan after opening a malicious e-mail disguised as notice from the IRS about “unreported income” (see New IRS Scam Could Be Costly).
Zeus Trojan Infiltrates Bank Security Firm, Oct. 6, 2009 — On Sept. 1, security industry start-up Silver Tail Systems held an in-depth online seminar for its bank and e-commerce clients that examined the stealth and sophistication of Zeus, a data-stealing Trojan horse program that organized thieves have used in a string of lucrative cyber heists this year. A week later, Silver Tail learned that Zeus had infiltrated its own network defenses.
New IRS Scam Could be Costly Sept. 29, 2009 — A recent victim of the scam is Landfill Service Corp., a solid waste company based in Apalachin, NY. Last week, the firm discovered that thieves had used Zeus to steal the company’s Internet banking credentials, after the attackers transferred $150,000 from its online bank account in a series of sub-$10,000 payments to 20 so-called money mules, co-conspirators around the country hired in job scams.
Cyber Gangs Hit Healthcare Providers Sept. 28, 2009 — Organized cyber thieves that have stolen millions from corporations and schools over the past few months recently defrauded several health care providers, including a number of non-profit organizations that cater to the disabled and the uninsured.
‘Money Mule’ Recruitment Network Exposed Sept. 24, 2009 — Security Fix interviewed one of the mules hired to receive money from Sanford School District, a small school system in Colorado that was robbed of $117,000 last month when hackers used the district’s online banking credentials to send sub-$10,000 payments to this mule and 16 others. The mule I spoke with said she was hired by a company called the Scope Group Inc., which claimed to be a nearly 20-year-old investment firm operating out of New York.
Maine Firm Sues Bank After $588,000 Cyber Heist Sept. 23, 2009 — A construction firm in Maine is suing a local bank after cyber thieves stole more than a half million dollars from the company in a sophisticated online bank heist.
Data Breach Highlights Role of ‘Money Mules’ Sept. 16, 2009 — On Friday, Brunswick, Maine-based heating and hardware firm Downeast Energy & Building Supply sent a letter notifying at least 850 customers that the company had suffered a data breach. Downeast sent the notice after discovering that hackers had broken in and stolen more than $200,000 from the company’s online bank account.
Cyber Crooks Target Public and Private Schools Sept. 14, 2009 — A gang of organized cyber criminals that has stolen millions from businesses across the United States over the past month appears to have turned its sights on public schools and universities. On the morning of Aug. 17, hackers who had broken into computers at the Sanford School District in tiny Sanford, Colorado initiated a batch of bogus transfers out of the school’s payroll account. Each of the transfers was kept just below $10,000 to avoid banks’ anti-money laundering reporting requirements, and went out to at least 17 different accomplices or “money mules” that the attackers had hired via work-at-home job scams.
Clamping Down on the ‘Clampi’ Trojan Sept. 11, 2009 — Finding the notorious Clampi banking Trojanon a computer inside your network is a little like spotting a single termite crawling into a crack in the wall: Chances are, the unwelcome little intruder is part of a much larger infestation. At least, that’s the story told by two businesses which recently discovered Clampi infections, compromises that handed organized cyber gangs the access they needed to steal tens of thousands of dollars. In early August, attackers used Clampi to swipe the online banking credentials assigned to the Sand Springs Oklahoma School District. The thieves then submitted a series of bogus payroll payments, totaling more than $150,000, to accomplices they had hired throughout the United States.Ferma-thumb-250×189
 Cyber Thieves Steal $447,000 from Wrecking Firm Sept. 9, 2009 — In mid-July, computer crooks stole $447,000 from Ferma Corp., a Santa Maria, Calif.-based demolition company, by initiating a large batch of transfers from Ferma’s online bank account to 39 “money mules,” willing or unwitting accomplices who typically are ensnared via job search Web sites into bogus work-at-home schemes.
Cyber Thieves Steal $447,000 from Wrecking Firm Sept. 9, 2009 — In mid-July, computer crooks stole $447,000 from Ferma Corp., a Santa Maria, Calif.-based demolition company, by initiating a large batch of transfers from Ferma’s online bank account to 39 “money mules,” willing or unwitting accomplices who typically are ensnared via job search Web sites into bogus work-at-home schemes.
More Business Banking Victims Speak Out Sept. 4, 2009 — David Johnston, owner of Sign Designs, Inc., a Modesto, Calif.-based company that makes and installs electric signs, said his company lost nearly $100,000 on July 23, when crooks used the company’s credentials to log in to its online banking account and initiate a series of transfers to 17 accomplices at seven banks around the country.
European Cyber-Gangs Target Small U.S. Firms, Group Says Aug. 25, 2009 — Organized cyber-gangs in Eastern Europe are increasingly preying on small and mid-size companies in the United States, setting off a multimillion-dollar online crime wave that has begun to worry the nation’s largest financial institutions.
Businesses Reluctant to Report Online Banking Fraud Aug. 25, 2009 — As grave as that sounds, the actual losses from this increasingly common type of online crime almost certainly are far higher. Those estimates were based on figures reported by the banks to federal regulators and law enforcement. But part of the problem, as Security Fix has found firsthand, is that many businesses are extremely wary about acknowledging that they’ve been victimized at all, even to federal investigators.
Tighter Security Urged for Businesses Banking Online Aug. 24, 2009 — An industry group representing some of nation’s largest banks sent a private alert to its members last week warning about a surge in reported cybercrime targeting small to mid-sized business. The advisory, issued by the Financial Services Information Sharing and Analysis Center, recommends that commercial banking customers take some fairly rigorous steps to secure their online banking accounts.
The Growing Threat to Business Banking Online July 20, 2009 — Federal investigators are fielding a large number of complaints from organizations that are being fleeced by a potent combination of organized cyber crooks abroad, sophisticated malicious software and not-so-sophisticated accomplices here in the United States, Security Fix has learned. The attacks also are exposing a poorly-kept secret in the commercial banking business: That companies big and small enjoy few of the protections afforded to consumers when faced with cyber fraud.Bullittcar-thumb-250×110
PC Invader Costs Ky. County $415,000 July 2, 2009 — Cyber criminals based in Ukraine stole $415,000 from the coffers of Bullitt County, Kentucky this week. The crooks were aided by more than two dozen co-conspirators in the United States, as well as a strain of malicious software capable of defeating online security measures put in place by many banks.
An Odyssey of Fraud June 17, 2009 — Andy Kordopatis is the proprietor of Odyssey Bar, a modest watering hole in Pocatello, Idaho, a few blocks away from Idaho State University. Most of his customers pay for their drinks with cash, but about three times a day he receives a phone call from someone he’s never served — in most cases someone who’s never even been to Idaho — asking why their credit or debit card has been charged a small amount by his establishment. Kordopatis says he can usually tell what’s coming next when the caller immediately asks to speak with the manager or owner.
Series: McColo
Major Source of Online Scams and Spams Knocked Offline Nov. 11, 2008 — A U.S. based Web hosting firm that security experts say was responsible for facilitating more than 75 percent of the junk e-mail blasted out each day globally has been knocked offline following reports from Security Fix on evidence gathered about suspicious activity emanating from the network. For the past four months, Security Fix has been gathering data from the security industry about McColo Corp., a San Jose, Calif., based Web hosting service whose client list experts say includes some of the most disreputable cyber-criminal gangs in business today. 
Spam Volumes Drop By Two-Thirds After Firm Goes Offline Nov. 12, 2008 — The volume of junk e-mail sent worldwide plummeted on Tuesday after a Web hosting firm identified by the computer security community as a major host of organizations engaged in spam activity was taken offline. (Note: A link to the full story on McColo’s demise is available here.)
A Closer Look at McColo Nov. 13, 2008 — In trying to get a sense of the activity attributed to McColo, I put together a flow chart, or mind map, showing McColo’s relationship to various sites associated with botnet activity, spam, pharmacy domains, etc
How Does So Much Spam Come From One Place? Nov. 18, 2008 — By nearly all accounts, spam volumes have remained at far diminished levels, though experts interviewed for this story expect spam to soon bounce back or even exceed previous levels. But the question remains: How could such a massive concentration of spam activity be hosted for so long from the servers at a single U.S.-based facility, in the belly of the security and tech community in Silicon Valley? The answer exemplifies how complex the battle against spam has become. Like other Internet hosting firms, McColo — which has not been charged with any crime and has been unavailable for comment — assigns certain Internet addresses for its clients’ computers to use. In effect, that’s how those firms operate on the Web.
Web Fraud 2.0: Faking your Internet Address Nov. 20, 2008 — One of the casualties from the unplugging of McColo Corp. is fraudcrew.com, a Web service that offered paying customers the ability to hide their identities online by routing their traffic through computers controlled by others.
Two Weeks Out, Spam Volumes Still Way Down Nov. 25, 2008 — A full two weeks after a Web hosting firm identified by the computer security community as a major host of organizations engaged in spam activity was taken offline, the volume of spam sent globally each day has yet to bounce back.
Spam Volumes Expected to Rise with Botnet Resurrection Nov. 26, 2008 — Spam volumes could rise considerably over the next few days now that one of the world’s largest networks of compromised computers used for blasting out junk e-mail was brought back to life tonight.
Srizbi Botnet Re-Emerges Despite Security Firm’s Best Efforts Nov. 26, 2008 — In the fallout resulting from knocking McColo Corp. offline, this past week may prove to be a missed opportunity in the prevention of a dramatic reappearance of junk e-mail, as a botnet that once controlled 40 percent of the world’s spam apparently has found a new home.
 Retail Fraud Rates Plummeted the Night McColo Went Offline Dec. 11, 2008 — It is unclear whether the decrease in retail fraud is related to the McColo situation, but in speaking with Ori Eisen, founder of 41st Parameter, he said close to a quarter of a million dollars worth of fraudulent charges that his customers battle every day came to a halt. “It stopped completely that night,” Eisen said, referring to a drop in fraudulent activity linked to purchases of high-value merchandise with stolen credit and debit cards on Nov. 11, the day McColo was shut down. “Yet, it will come back after [the scammers] erect their new infrastructure.”Mcooze-thumb-250×135
Retail Fraud Rates Plummeted the Night McColo Went Offline Dec. 11, 2008 — It is unclear whether the decrease in retail fraud is related to the McColo situation, but in speaking with Ori Eisen, founder of 41st Parameter, he said close to a quarter of a million dollars worth of fraudulent charges that his customers battle every day came to a halt. “It stopped completely that night,” Eisen said, referring to a drop in fraudulent activity linked to purchases of high-value merchandise with stolen credit and debit cards on Nov. 11, the day McColo was shut down. “Yet, it will come back after [the scammers] erect their new infrastructure.”Mcooze-thumb-250×135
A Year Later: A Look Back at McColo Nov. 11, 2009 — A review of more than 3,000 Internet addresses previously assigned to the hosting firm reveals an Internet ghost town, as if the entire neighborhood had been contaminated by some kind of toxic sludge that frightened off any potential future occupants.
Series: 3FN/Pricewert
FTC Sues, Shuts Down N. Calif. Web Hosting Firm June 4, 2009 — Sometime on Tuesday, more than 15,000 Web sites connected to San Jose, Calif., based Triple Fiber Network (3FN.net) went dark. 3FN’s sites were disconnected after a Northern California district court judge approved an FTC request to have the company’s upstream Internet providers stop routing traffic for the provider.
The Fallout from the 3FN Takedown Jun. 10, 2009 — The Federal Trade Commission’s unprecedented recent takedown against troubled Web hosting provider 3FN.net has had an immediate – if little noticed – impact on the level of spam sent worldwide, and the number of infected PCs doing the spamming, according to multiple sources. Experts say the drop in spam probably is not visible to most Internet users or even operators of large networks, as the decrease is within the upper ranges of daily fluctuations in spam volumes. Still, the preliminary results indicate that a large number of spam-spewing zombie PCs were being coordinated out of severs hosted at 3FN.
 Following the Money: Rogue Anti-Virus Software July 31, 2009 — By its very nature, the architecture and limited rules governing the Web make it difficult to track individuals who might be involved in improper activity. Cyber-sleuths often must navigate through a maze of dead-end records, pseudonyms or anonymous corporations, usually based overseas. The success rate is fairly low. Even if you manage to trace one link in the chain — such as a payment processor or Web host — the business or person involved claims that he or she was merely providing a legal service to an unknown client who turns out to be a scammer. But every so often, subtle links between the various layers suggest a more visible role by various parties involved. This was what I found recently, when I began investigating a Web site name called innovagest2000.com.
Following the Money: Rogue Anti-Virus Software July 31, 2009 — By its very nature, the architecture and limited rules governing the Web make it difficult to track individuals who might be involved in improper activity. Cyber-sleuths often must navigate through a maze of dead-end records, pseudonyms or anonymous corporations, usually based overseas. The success rate is fairly low. Even if you manage to trace one link in the chain — such as a payment processor or Web host — the business or person involved claims that he or she was merely providing a legal service to an unknown client who turns out to be a scammer. But every so often, subtle links between the various layers suggest a more visible role by various parties involved. This was what I found recently, when I began investigating a Web site name called innovagest2000.com.
Series: Web Fraud 2.0
Web Fraud 2.0: Franchising Cyber Crime June 19, 2009 — For the most part, cyber gangs that create malicious software and spread spam operate as shadowy, exclusive organizations that toil in secrecy, usually in Eastern Europe. But with just a few clicks, anyone can jump into business with even the most notorious of these organizations by opening up the equivalent of a franchise operation.
Web Fraud 2.0: Data Search Tools for ID Thieves Mar. 23, 2009 — Data such as your Social Security number, mother’s maiden name and credit card balance are not as difficult for ID thieves to find as most people think. I’ve recently learned that cyber crooks are providing cheap, instant access to detailed consumer databases, offering identity thieves the ability to find missing data as they compile dossiers on targeted individuals. Security Fix spent the past week testing services offered by two Web sites that sell access to a wealth of information on consumers. Each site offers free registration, but requires users to fund their accounts via Webmoney, a PayPal-like virtual currency that is popular in Russia and Eastern Europe.
Rogue Antivirus Distribution Network Dismantled Mar. 20, 2009 — A major distribution network for rogue anti-virus products has been shut down following reports by Security Fix about massive profits that the network’s affiliates were making for disseminating the worthless software.TCaff4-thumb-286×181
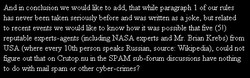
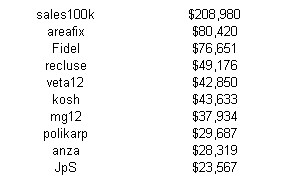 Massive Profits Fueling Rogue Anti-Virus Market Mar. 16, 2009 — TrafficConverter.biz was dismantled on Nov. 29, 2008, most likely because the same domain was referenced deep inside the guts of the Conficker worm, a family of malware that is estimated to have infected at least 10 million Microsoft Windows systems. The graphics below show the Top 10 earners in the TrafficConverter program, Some of the biggest earners made more than $330,000 a month in commissions.
Massive Profits Fueling Rogue Anti-Virus Market Mar. 16, 2009 — TrafficConverter.biz was dismantled on Nov. 29, 2008, most likely because the same domain was referenced deep inside the guts of the Conficker worm, a family of malware that is estimated to have infected at least 10 million Microsoft Windows systems. The graphics below show the Top 10 earners in the TrafficConverter program, Some of the biggest earners made more than $330,000 a month in commissions.
Web Fraud 2.0: Thwarting Anti-Spam Defenses Aug. 25, 2008 — Spammers have made great strides this past year in defeating CAPTCHAs, the distorted text used as a security test to ensure a person and not a machine is behind a computer screen. But automated programs that spammers use to thwart CAPTCHAs still aren’t nearly as successful as the practice of hiring thousands of people to do nothing but remotely solve the puzzles for clients.
Web Fraud 2.0: Distributing Your Malware Aug. 22, 2008 — The allure of cyber crime lies in its promise of quick riches, much like that of the illegal drug trade. But building a network of hacked personal computers that can distribute your data-stealing malicious software is a time-consuming process that requires a modicum of skill. That is, until recently, when several online services have emerged that promise to help would-be cyber crooks graduate from common street dealers to distributors overnight.Scanlab1-thumb-228×158
 Web Fraud 2.0: Digital Forgeries Aug. 21, 2008 — For businesses, positively identifying someone online – by name, or physical location – is extremely difficult. Many Internet firms seek to verify the identity of customers by requesting scanned copies of their driver’s licenses, passports, or utility bills. But what if services aimed at creating counterfeit versions of these documents became widespread? How long would businesses continue to rely on this method of identification?
Web Fraud 2.0: Digital Forgeries Aug. 21, 2008 — For businesses, positively identifying someone online – by name, or physical location – is extremely difficult. Many Internet firms seek to verify the identity of customers by requesting scanned copies of their driver’s licenses, passports, or utility bills. But what if services aimed at creating counterfeit versions of these documents became widespread? How long would businesses continue to rely on this method of identification?
Web Fraud 2.0: Validating Your Stolen Goods Aug. 20, 2008 — If there is any truth to the old saying that there is no honor among thieves then it is doubly true for thieves who transact with one another yet never actually meet face-to-face. Perhaps that explains the popularity of certain services in the underground cyber crime economy that make it easy for crooks to purchase stolen credit and bank accounts in bulk and check whether the accounts are legitimate and active.
Web Fraud 2.0: Cloaking Connections Aug. 19, 2008 — These days, nearly every aspect of the underground online economy that supports commercial crime operations has been automated. Online forums and criminal social networking sites have long offered aspiring newbies tips on getting started. But a slew of extremely popular Web sites increasingly are making it possible for newcomers to begin reaping profits from their activities through point-and-click Web interfaces that even the most novice hackers can navigate. What follows today and throughout the rest of the week is a look at some trends and tools Security Fix observed being used by cyber crooks, as a result of several months of lurking on some of the more popular (and in some cases invite-only) cyber criminal forums.
RoboTraff: A Hacker’s Go-To for Clicks May 7, 2008 — Anyone who doubts that Internet click fraud has become a big money maker should take a look at a Russian Web site called Robotraff.com, which bills itself as “the first stock exchange of Web traffic.” Set up a free account at Robotraff and you’re ready to buy or sell Web traffic. Got 30,000 hacked personal computers under your thumb? Super! Now you can use those systems to generate a steady income just by pointing them at Web sites requested by a buyer.
Series: The Russian Business Network (RBN)
Shadowy Russian Firm Seen as Conduit for Cybercrime Oct. 13, 2007 — An Internet business based in St. Petersburg has become a world hub for Web sites devoted to child pornography, spamming and identity theft, according to computer security experts. They say Russian authorities have provided little help in efforts to shut down the company.
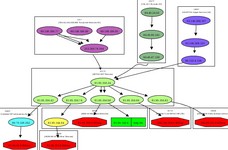 Mapping the Russian Business Network Oct. 13, 2007 — I thought it might be useful to name the companies that provide RBN’s direct upstream Internet connectivity, as well as a few major Internet providers that provide services to RBN, including Tiscali.uk, SBT Telecom, Aki Mon Telecom and Nevacon LTD. The graph at the right is not an exhaustive look at all of the companies providing networking services to RBN, and it does not imply that the network providers listed are aware of or condone any illegal activity by RBN or RBN’s customers.
Mapping the Russian Business Network Oct. 13, 2007 — I thought it might be useful to name the companies that provide RBN’s direct upstream Internet connectivity, as well as a few major Internet providers that provide services to RBN, including Tiscali.uk, SBT Telecom, Aki Mon Telecom and Nevacon LTD. The graph at the right is not an exhaustive look at all of the companies providing networking services to RBN, and it does not imply that the network providers listed are aware of or condone any illegal activity by RBN or RBN’s customers.
Taking on the Russian Business Network Oct. 13, 2007 — John decided to completely block RBN from traversing his network in June, roughly a year after noticing a huge uptick in the number of his customers infected by computer worms, viruses and information-stealing programs that through one route or another fed stolen data back to networks hosted on RBN.”We played Whak-a-Mole with RBN for about a year, until I got tired of shutting down or cleaning up customers who were compromised after visiting one of these Russian addresses,” John said.
Russian Business Network: Down, but Not Out Nov. 7, 2007 — A major Russian Internet service provider whose client list amounted to a laundry list of organized cyber crime operations appears to have closed shop. But security experts caution that there are signs that the highly profitable network may already be building a new home for itself elsewhere on the Web.
Series: Estdomains/Esthost
 EstDomains: A Sordid History and a Storied CEO Sept. 8, 2008 — It seems Mr. Tsastsin has a rather colorful past, and is no stranger to organized crime. According to the local court and news media, he was recently sentenced to three years in an Estonian prison after being found guilty of credit card fraud, document forgery, and money laundering. A Feb. 6 story from Eesti Päevaleht — “Estonian Daily,” one of Estonia’s two major dailies – explains the backstory. I couldn’t find any version of this story that had ever been published in English, so I had it professionally translated by Koit Ojamaa, a former Estonian citizen who now lives near the Washington D.C. area.
EstDomains: A Sordid History and a Storied CEO Sept. 8, 2008 — It seems Mr. Tsastsin has a rather colorful past, and is no stranger to organized crime. According to the local court and news media, he was recently sentenced to three years in an Estonian prison after being found guilty of credit card fraud, document forgery, and money laundering. A Feb. 6 story from Eesti Päevaleht — “Estonian Daily,” one of Estonia’s two major dailies – explains the backstory. I couldn’t find any version of this story that had ever been published in English, so I had it professionally translated by Koit Ojamaa, a former Estonian citizen who now lives near the Washington D.C. area.
A Superlative Scam and Spam Site Registrar Sept. 8, 2008 — Over the past week, a number of the Internet’s largest data carriers have ceased providing online connectivity to Atrivo (a.k.a. “Intercage”), an ISP that security experts say is home to a huge number of scammers and spammers. This week, I’m turning the spotlight on EstDomains Inc., Atrivo’s most important customer and the single biggest reason so many experts have condemned Atrivo.
ICANN De-Accredits EstDomains for CEO’s Fraud Convictions Oct. 29, 2008 — The entity responsible for overseeing the Internet’s domain name system said Tuesday that it was revoking the right of registrar EstDomains.com to process new domain names, citing the company CEO’s recent conviction on cyber crime charges.
Series: Atrivo/Intercage
Report Slams U.S. Host as Major Source of Badware Aug. 28, 2008 — Last week, I examined a series of Web services that make profiting from cyber crime a point-and-click exercise that even the most novice hackers can master. Today, I’d like to highlight the activities of Atrivo, a Concord, Calif., based network provider that hosts some of these services.Glbxdepeer-thumb-228×203
 Scammer-Heavy U.S. ISP Grows More Isolated Sept. 5, 2008 — Last week, Security Fix published an analysis of Atrivo, a California based Internet service provider, also known as Intercage, that has proven to be a virtual magnet for cyber-criminal operations. Since that time, Atrivo’s biggest network backbone provider decided it could no longer support the company, and stopped offering it direct connectivity.
Scammer-Heavy U.S. ISP Grows More Isolated Sept. 5, 2008 — Last week, Security Fix published an analysis of Atrivo, a California based Internet service provider, also known as Intercage, that has proven to be a virtual magnet for cyber-criminal operations. Since that time, Atrivo’s biggest network backbone provider decided it could no longer support the company, and stopped offering it direct connectivity.
Internet Shuns U.S. Based ISP Amid Fraud, Abuse Allegations Sept. 22, 2008 — A California based commercial Internet service provider whose clients included a laundry list of spammers and scammers is now offline, after the last of the company’s upstream Internet providers decided to the pull the plug. Atrivo, a.k.a “Intercage,” of Northern California, ceased to be reachable from any points on the Internet early Sunday morning when the ISP’s sole remaining provider – Pacific Internet Exchange (PIE) – stopped routing traffic for the troubled company.
Spam Volumes Plummet After Atrivo Shutdown Oct. 9, 2008 — Security Fix has spilled quite a bit of digital ink chronicling the demise of Atrivo (a.k.a. “Intercage”), a now-defunct Northern Calif. based Internet service provider that served as home base for a large number of cyber criminal operations. Happily, data released this week about a short-lived but precipitous decline in the level of badness online after Atrivo was shut down illustrates just how bad Atrivo was.
Atrivo Shutdown Hastened Demise of Storm Worm Oct. 17, 2008 — The infamous Storm worm, which powered a network of thousands of compromised PCs once responsible for sending more than 20 percent of all spam, appears to have died off. Security experts say Storm’s death knell was sounded by the recent shutdown of Atrivo, a California based ISP that was home to a number of criminal cyber crime operations, including at least three of the master servers used to control the Storm network.
Other Top Security Stories
Former Anti-virus Researcher Turns Tables on Industry Oct. 27, 2009 — A security researcher shunned by the anti-virus community for violating its unwritten rules has attempted to turn the tables, erecting a Web service that virus writers could use to make their creations more stealthy and undetectable for longer periods of time.
PayChoice Suffers Another Data Breach Oct. 15, 2009 — Payroll services provider PayChoice took its Web-based service offline for the second time in a month on Wednesday in response to yet another data breach caused by hackers.
Hackers Breach Payroll Giant, Target Customers Sept. 30, 2009 — Hackers last week apparently used stolen account information from a New Jersey company that provides online payroll services to target the firm’s customers in a scheme to steal passwords and other information. Moorestown, N.J. based PayChoice, provides direct payroll processing services and licenses its online employee payroll management product to at least 240 other payroll processing firms, serving 125,000 organizations.
Network Solutions Hack Compromises 573,000 Credit, Debit Accounts July 24. 2009 — Hackers have broken into Web servers owned by domain registrar and hosting provider Network Solutions, planting rogue code that resulted in the compromise of more than 573,000 debit and credit card accounts over the past three months, Security Fix has learned.
PC Infections Often Spread to Web Sites July 16, 2009 — Most people are familiar with the notion that a computer virus can be passed from PC to PC, but many folks would probably be surprised to learn that a sick PC can often pass its infection on to Web sites, too. Some of the most pervasive malicious software circulating today (e.g., Virut) includes spreading capabilities that hark back to the file-infecting methods of the earliest viruses, which spread by making copies of themselves, or by inserting their code into other files on the host system.
PCs Used in Korea DDoS Attacks May Self Destruct July 9, 2009 — There are signs that the concerted cyber attacks targeting U.S. and Korean government and commercial Web sites this past week are beginning to wane. Yet, even if the assaults were to be completely blocked tomorrow, the attackers could still have one last, inglorious weapon in their arsenal: New evidence suggests that the malicious code responsible for spreading this attack includes instructions to overwrite the infected PC’s hard drive.
The Scrap Value of a Hacked PC May 26, 2009 — Computer users often dismiss Internet security best practices because they find them inconvenient, or because they think the rules don’t apply to them. Many cling to the misguided belief that because they don’t bank or shop online, that bad guys won’t target them. The next time you hear this claim, please refer the misguided person to this blog post, which attempts to examine some of the more common — yet often overlooked — ways that cyber crooks can put your PC to criminal use.
Heartland Breach Blamed for Failed Membership Renewals May 14, 2009 — In February, Bill Oesterle began seeing nearly twice the normal number of transactions being declined for customers who had set up auto-billing on their accounts. The co-founder of Angie’s List — a service that aggregates consumer reviews of local contractors and physicians — said he originally assumed more customers were simply having trouble making ends meet in a down economy.
Zeustracker and the Nuclear Option May 7, 2009 — One of the scarier realities about malicious software is that these programs leave ultimate control over victim machines in the hands of the attacker, who could simply decide to order all of the infected machines to self-destruct. Most security experts will tell you that while this so-called “nuclear option” is an available feature in some malware, it is hardly ever used. Disabling infected systems is counterproductive for attackers, who generally focus on hoovering as much personal and financial data as they can from the PCs they control. But try telling that to Roman Hüssy, a 21-year-old Swiss information technology expert, who last month witnessed a collection of more than 100,000 hacked Microsoft Windows systems tearing themselves apart at the command of their cyber criminal overlords.
Hackers Break into Virginia Health Professions Database, Demand Ransom May 4, 2009 — Hackers last week broke into a Virginia state Web site used by pharmacists to track prescription drug abuse. They deleted records on more than 8 million patients and replaced the site’s homepage with a ransom note demanding $10 million for the return of the records, according to a posting on Wikileaks.org, an online clearinghouse for leaked documents.
Experts Chart Spike in Cyber Sieges May 1, 2009 — Cyber attacks with enough firepower to knock entire countries off the Internet have spiked in recent months, raising fresh concerns within the security community about weaknesses in the Internet infrastructure that help create such weapons of mass disruption.
IRS Awards Tax Payment Contract to RBS Worldpay Apr. 23, 2009 — The Internal Revenue Service has awarded a contract to process tax return payments for the coming filing season to RBS Worldpay, a company that recently disclosed that a hacker break-in jeopardized financial data on 1.5 million payroll card holders and at least 1.1 million Social Security numbers.
Organized Crime Behind a Majority of Data Breaches Apr. 15, 2009 — A string of data breaches orchestrated principally by a handful of organized cyber-crime gangs translated into the loss of hundreds of millions of consumer records last year, security experts say.
Why Web Security Matters to Us All Mar. 6, 2009 — For the past several months, some of the sharpest minds in the security community have teamed up to block cyber criminals from wresting control over what may be one of the largest armies of hacked computers ever built. While those efforts are ongoing and so far appear effective, all of that work could be undone thanks to the lax security of a single Web site.PH2009030202951
To (& From) Russia, With Love Mar. 3, 2009 — If you ask security experts why more cyber criminals aren’t brought to justice, the answer you will probably hear is that U.S. authorities simply aren’t getting the cooperation they need from law enforcement officials in Russia and other Eastern European nations, where some of the world’s most active cyber criminal gangs are thought to operate with impunity. But I wonder whether authorities in those countries would be any more willing to pursue cyber crooks in their own countries if they were forced to confront just how deeply those groups have penetrated key government and private computer networks in those regions?
When Cyber Criminals Eat Their Own Jan. 26, 2009 — Some of the most prolific and recognizable malware disbursed by Russian and East European cyber crime groups purposefully avoids infecting computers if the program detects the potential victim is a native resident. But evidence from the Conficker worm — which by some estimates is infecting more than one million new PCs each day — shows that trend may be shifting.
Payment Processor Breach May Be Largest Ever Jan. 20, 2009 — A data breach last year at Princeton, N.J., payment processor Heartland Payment Systems may have compromised tens of millions of credit and debit card transactions, the company said today. If accurate, such figures may make the Heartland incident one of the largest data breaches ever reported.
Move Over, Client #9 Jan. 19, 2009 — A popular Web site that helps connect young women with so-called “Sugar Daddies” has fixed a major security hole that – apparently since its inception two years ago — allowed anyone with a Web browser to view the private negotiations between site members.
 Popular Mechanics: Who’s Tracking You? Jan. 2009 — While Barack Obama has selected key members of his national security team—Defense Secretary, National Security Adviser and Secretary of State—there are calls for the president-elect to make another security appointment. The bipartisan Commission on Cybersecurity for the 44th Presidency suggests that there is a dire need to create a National Office for Cyberspace to protect our nation’s most sensitive computer networks. The need for national cyberspace security is a no-brainer, but who is going to protect us from the digital devices that organize our lives and leaves personal information vulnerable to theft? Here, a behind-the-scenes look at how hackers are unearthing the private details of our lives by attacking our web browsers, cell phones, and personal electronics.
Popular Mechanics: Who’s Tracking You? Jan. 2009 — While Barack Obama has selected key members of his national security team—Defense Secretary, National Security Adviser and Secretary of State—there are calls for the president-elect to make another security appointment. The bipartisan Commission on Cybersecurity for the 44th Presidency suggests that there is a dire need to create a National Office for Cyberspace to protect our nation’s most sensitive computer networks. The need for national cyberspace security is a no-brainer, but who is going to protect us from the digital devices that organize our lives and leaves personal information vulnerable to theft? Here, a behind-the-scenes look at how hackers are unearthing the private details of our lives by attacking our web browsers, cell phones, and personal electronics.
Researchers Hack Internet Security Infrastructure Dec. 30, 2008 — An international team of computer security researchers demonstrated today a key weakness in the Internet infrastructure that could let hackers launch virtually undetectable attacks aimed at intercepting secured online communications when consumers visit bank and e-commerce Web sites.
Hashing Over Tiny Details Dec. 30, 2008 — Building on research from 2004 and 2007, an international team of mathematicians and cryptographers sought to exploit vulnerabilities within RapidSSL, to duplicate the cryptographic signature the company uses to certify secure socket layer (SSL) certificates.
Digging Deeper into the CheckFree Attack Dec. 6, 2008 — Interestingly, CheckFree.com was not the only site that the attackers hijacked and redirected back to the Ukrainian server. Tacoma, Wash., based anti-phishing company Internet Identity found at least 71 other domains pointing to the same Ukranian address during that same time period. Of those, 69 were registered at either eNom or Network Solutions, and all appeared to be legitimate domains that had been hijacked.
Hackers Hijacked Large E-Bill Payment Site Dec. 3, 2008 — Hackers on Tuesday hijacked the Web site CheckFree.com, one of the largest online bill payment companies, redirecting an unknown number of visitors to a Web address that tried to install malicious software on visitors’ computers, the company said today.Abp-thumb-250×327
 Pharmacy Extortionists Take on CIA, DoD, FBI, NSA Nov. 24, 2008 — Extortionists targeting clients of Express Scripts — one of the nation’s largest pharmacy benefits management firms — may have inadvertently picked a fight for which they were ill-prepared. Security Fix has learned that among the company’s biggest customers is the federal government, and specifically almost every federal law enforcement, military and intelligence agency in the country.
Pharmacy Extortionists Take on CIA, DoD, FBI, NSA Nov. 24, 2008 — Extortionists targeting clients of Express Scripts — one of the nation’s largest pharmacy benefits management firms — may have inadvertently picked a fight for which they were ill-prepared. Security Fix has learned that among the company’s biggest customers is the federal government, and specifically almost every federal law enforcement, military and intelligence agency in the country.
Network Identity Theft Politely Avenged Nov. 18, 2008 — A massive swath of some 65,536 unique Internet addresses that appear to have been swiped from early Internet pioneers by a convicted spammer has been reclaimed by Internet regulators, Security Fix has learned.
Q&A with FBI’s Cyber Division Chief Aug. 18, 2008 — At the end of the Black Hat hacker convention in Las Vegas a week ago Thursday, I had a few minutes to sit down with James Finch, head of the FBI’s Cyber Division. What follows is an excerpted Q&A from that discussion, in which Finch describes himself as a serious geek who refuses to be spooked by organized cyber criminal gangs that target online banking customers and other ‘Netizens.
Speeding in Maryland Could be Hazardous to Your Identity July 11, 2008 — If you’ve ever received a traffic ticket in Maryland, your name, birthday, Social Security number and address may be posted on the Maryland state Web site for anyone to find, Security Fix has learned.
Justice Breyer is Among Victims in Data Breach Cause by File Sharing July 9, 2008 — Sometime late last year, an employee of a McLean investment firm decided to trade some music, or maybe a movie, with like-minded users of the online file-sharing network LimeWire while using a company computer. In doing so, he inadvertently opened the private files of his firm, Wagner Resource Group, to the public.
Amazon: Hey Spammers, Get Off My Cloud! July 1, 2008 — I am accustomed to receiving e-mail from Amazon.com, as I am a fiercely loyal customer who shops there quite frequently. But it took me by surprise this weekend to discover that mounds of porn spam and junk e-mail laced with computer viruses are actively being blasted from digital real estate leased to the e-commerce giant.
Anonymous Domain Sales: A Spammer’s Delight June 17, 2008 — Spammers routinely register their sites under false names, or hijack someone else’s identity to do so. But new research shows they’re also paying for premium services when registering domain names to ensure a deeper level of anonymity.
Cyber Incident Blamed for Nuclear Plant Shutdown June 5, 2008 — A nuclear power plant in Georgia was recently forced into an emergency shutdown for 48 hours after a software update was installed on a single computer. The incident occurred on March 7 at Unit 2 of the Hatch nuclear power plant near Baxley, Georgia. The trouble started after an engineer from Southern Company, which manages the technology operations for the plant, installed a software update on a computer operating on the plant’s business network.
Beware Error Messages at Bank Sites June 2, 2008 — If you own or work at a small to mid-sized business, and are presented with an error message about data synchronization or site maintenance when trying to access your company’s bank account online, you might want to give the bank a call: A criminal group that specializes in deploying malicious software to steal banking data is presenting victims with fake maintenance pages and error messages as a means of getting around anti-fraud safeguards erected by many banks.
Most Spam Sites Tied to a Handful of Registrars May 19, 2008 — New research suggests that more than three quarters of all Web sites advertised through spam are clustered at just 10 domain name registrars.
A Case of Network Identity Theft? Apr. 28, 2008 — Digital real estate leased to one of the Internet’s oldest landholders appears to have been quietly seized by e-mail marketers closely associated with an individual once tagged by anti-spam groups as one of the world’s most notorious spammers. What’s remarkable about this case study is that it pits a vocal spammer against the American Registry for Internet Numbers, which has yet to take action. ARIN is one of five regional Internet registries worldwide that is responsible for allocating IP addresses (ARIN handles this process for the United States, Canada and 22 Caribbean countries).
Identity Theft Smash & Grab, CEO Style Apr. 15, 2008 — Tens of thousands of corporate executives were the target of a series of identity-theft scams this week, e-mail-borne schemes that appear to have netted close to 2,000 victims so far.
 The Curious Case of Dmitry Golubov Mar. 28, 2008 — Earlier this month, Security Fix took a look at Dmitry Ivanovich Golubov, a Ukrainian politician once considered by U.S. law enforcement to be a top cybercrime boss. Golubov took rather strong exception to the way he was characterized in that post, denying involvement in any type of cybercrime activity. The problem, Golubov claimed, is that the FBI confused him with someone else.
The Curious Case of Dmitry Golubov Mar. 28, 2008 — Earlier this month, Security Fix took a look at Dmitry Ivanovich Golubov, a Ukrainian politician once considered by U.S. law enforcement to be a top cybercrime boss. Golubov took rather strong exception to the way he was characterized in that post, denying involvement in any type of cybercrime activity. The problem, Golubov claimed, is that the FBI confused him with someone else.
U.S.-Based ISPs Court Known Terror Groups as Clients Mar. 27, 2008 — Herndon, Va.-based Network Solutions said Wednesday that it suspended Hizbollah.org, an official site of Hezbollah, a Lebanese political and paramilitary group. Turns out, Network Solutions, which was one of the original firms in the domain registration business, was accepting payment for the domain in violation of a U.S. law that bars American companies from doing business with organizations listed by Uncle Sam as terrorist groups. Closer inspection also reveals that Network Solutions and other U.S.-based Internet service providers and domain registrars provide services to other groups on the government’s list of terrorist organizations.
They Told You Not to Reply Mar. 21, 2008 — When businesses want to communicate with their customers via e-mail, many send messages with a bogus return address, e.g. “somethinghere@donotreply.com.” The practice is meant to communicate to recipients that any replies will go unread. But when those messages are sent to an inactive e-mail address or the recipient ignores the instruction and replies anyway, the missives don’t just disappear into the digital ether. Instead, they land in Chet Faliszek’s e-mail box.
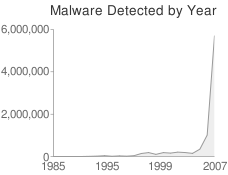 Anti-Virus Firms Scrambling to Keep Up Mar. 19, 2008 — The sheer volume and complexity of computer viruses being released on the Internet today has the anti-virus industry on the defensive, experts say, underscoring the need for consumers to avoid relying on anti-virus software alone to keep their home computers safe and secure. Approximately 5.5 million malicious software programs were unleashed on the Web last year, according to AV Test Labs, a German company that measures how quickly and accurately anti-virus products detect the latest malicious software, also known as “malware.”
Anti-Virus Firms Scrambling to Keep Up Mar. 19, 2008 — The sheer volume and complexity of computer viruses being released on the Internet today has the anti-virus industry on the defensive, experts say, underscoring the need for consumers to avoid relying on anti-virus software alone to keep their home computers safe and secure. Approximately 5.5 million malicious software programs were unleashed on the Web last year, according to AV Test Labs, a German company that measures how quickly and accurately anti-virus products detect the latest malicious software, also known as “malware.”
The Anatomy of a ‘Vishing’ Scam Mar. 15, 2008 — A series of well-orchestrated wireless phone-based phishing attacks against several financial institutions last week illustrates how scam artists are growing more adept at fleecing consumers by exploiting security holes in seemingly unrelated Internet technologies.
Ukrainian Cybercrime Boss Leads Political Party Mar. 13, 2008 — A Ukrainian man once known as one of the top ringleaders in Eastern Europe-based organized cyber crime is now heading up a new political party there. Dmitry Ivanovich Golubov, a 24-year-old from Odessa, is leading the upstart “Internet Party of Ukraine,” a party he helped create shortly after parliamentary elections in the country last fall. In 2005, Golubov — a.k.a. “script” — was arrested and jailed on charges of trading in credit and debit card credentials stolen via computer viruses and password-snatching Trojan horse programs, thefts that caused millions of dollars in losses to banks over several years.
‘Money Mules’ Help Haul Criminals’ Loot Jan. 25, 2008 — The e-mail offer of a work-at-home job was a godsend to Deena Monroe, a Statesville, N.C., single mom who had just been laid off from her position as a warehouse supervisor. The prospective employer said Monroe’s resume had been spotted on job search site Careerbuilder.com and offered her the chance to make a few hundred dollars a week completing sales for a marketing company based in Australia.
 Drawing a (Scary) Face on Malicious Software Jan. 18, 2008 — Dragulescu, a research assistant at the Massachusetts Institute of Technology’s Sociable Media Group, created his so-called “threat art” in conjunction with live malware intercepted by e-mail security firm MessageLabs. Each is disassembled into a dump of binary code and then run through a program Dragulescu wrote. That program spends a few hours crunching through all the data, looking for patterns in the code that will determine the shape, color and complexity of each piece of threat art.
Drawing a (Scary) Face on Malicious Software Jan. 18, 2008 — Dragulescu, a research assistant at the Massachusetts Institute of Technology’s Sociable Media Group, created his so-called “threat art” in conjunction with live malware intercepted by e-mail security firm MessageLabs. Each is disassembled into a dump of binary code and then run through a program Dragulescu wrote. That program spends a few hours crunching through all the data, looking for patterns in the code that will determine the shape, color and complexity of each piece of threat art.
Wishing an (Un)happy Birthday to the Storm Worm Jan. 17, 2008 — Dmitri Alperovitch, director of intelligence analysis and hosted security for San Jose, Calif.-based Secure Computing, said federal law enforcement officials who need to know have already learned the identities of those responsible for running the Storm worm network, but that U.S. authorities have thus far been prevented from bringing those responsible to justice due to a lack of cooperation from officials in St. Petersburg, Russia, where the Storm worm authors are thought to reside. In a recent investigative series on cyber crime featured on washingtonpost.com, St. Petersburg was fingered as the host city for one of the Internet’s most profligate and cyber-crime enabling operation — the Russian Business Network.
Cyber Crime 2.0 Dec. 20, 2007 — The year 2007 may go down in the annals of Internet crime as the year when organized cyber criminals finally got serious about their marketing strategies — crafting cyber schemes that were significantly more sophisticated and stealthy.
Credit Card Thieves Flood Wikimedia With Pennies Nov. 20, 2007 — The Wikimedia Foundation, the parent organization of the free online encyclopedia Wikipedia and other open-source projects, recently increased the minimum amount it will accept in donations after scammers apparently began testing the validity of stolen credit cards by sending a series of 1-cent “donations” to the group.
Salesforce.com Acknowledges Data Loss Nov. 6, 2007 — Business software provider Salesforce.com acknowledged that a recent spate of targeted e-mail virus and phishing attacks against its customers resulted from one of its own employees falling for a phishing scam and turning over the keys to the company’s customer database. On Oct. 19, Security Fix reported that payroll giant Automatic Data Processing (ADP) and several banks — including Suntrust — were among a number of institutions that were victimized by a series of highly-targeted phishing scams that addresses recipients by name and asked them to click on a link – which tried to download password-stealing malicious software.
Deconstructing the Fake FTC E-mail Virus Attack Nov. 5, 2007 — The person who masterminded this attack even took screen shots of his own desktop, presumably to test his malware to make sure it functioned properly (note that his Windows desktop is in Russian with Cyrillic characters). A short snippet of commands he typed on his own computer — along with his own IP address — also appeared in the cache of stolen data on the Web site where the Trojan horse uploads stolen data. The individual responsible for this virus lives in the Ukraine and writes his own malicious software.
 Contractor Blamed in DHS Data Breach Sept. 27, 2007 — The FBI is investigating a major information technology firm with a $1.7 billion Department of Homeland Security contract after it allegedly failed to detect cyber break-ins traced to a Chinese-language Web site and then tried to cover up its deficiencies, according to congressional investigators. At the center of the probe is Unisys Corp., a company that in 2002 won a $1 billion deal to build, secure and manage the information technology networks for the Transportation Security Administration and DHS headquarters. In 2005, the company was awarded a $750 million follow-on contract.
Contractor Blamed in DHS Data Breach Sept. 27, 2007 — The FBI is investigating a major information technology firm with a $1.7 billion Department of Homeland Security contract after it allegedly failed to detect cyber break-ins traced to a Chinese-language Web site and then tried to cover up its deficiencies, according to congressional investigators. At the center of the probe is Unisys Corp., a company that in 2002 won a $1 billion deal to build, secure and manage the information technology networks for the Transportation Security Administration and DHS headquarters. In 2005, the company was awarded a $750 million follow-on contract.
Is CyberCrime Really the FBI’s No. 3 Priority? Sept. 24, 2007 — The Federal Bureau of Investigation says that its No. 3 priority is protecting the United States “against cyber-based attacks and high-technology crimes.” Given the increasing pervasiveness and costs associated with such crime, FBI Director Robert Mueller should be commended for giving anti-cyber crime investigations such high status, second only to terrorism and espionage/counter intelligence investigations. But according to an analysis by Security Fix, cyber crime remains a distant third priority for the federal law enforcement agency, at least in terms of resources applied to the problem.
The Threat of Reputation-Based Attacks Sept. 18, 2007 — CastleCops.com is accustomed to being attacked by online crooks: The volunteer-led cybercrime-fighting group has endured nearly a month long siege by thousands of criminally-controlled PCs aimed at crippling its Web site. So when the latest attack failed to prevent legitimate users from visiting the site, the bad guys unveiled an unlikely secret weapon: bogus donations.
A Time Patch: Apple 2006 Sept. 4, 2007 — Apple computer users mostly stayed off the radar screens of the criminal hacker community in 2006, even as the Cupertino, Calif., software company learned of an unprecedented number of serious security holes in its Mac OS X systems and other software. At the same time, many of those same flaws have made Web surfing more precarious for Apple’s largest and fastest growing customer base — Microsoft Windows users.
Beware of 5-Star Vaporware Aug. 20, 2007 — U.K. computer programmer Andy Brice was proud of the awards and accolades his software had won from his peers online. That is, until he noticed that pretty much everyone else’s software received the same “5-star” rating and high praise from various software directories and download sites.
 Three Worked the Web to Help Terrorists: British Case Reveals How Stolen Credit Card Data Bought Supplies for Operatives July 5, 2007 — The global jihad landed in Linda Spence’s e-mail inbox during the summer of 2003, in the form of a message urging her to verify her eBay account information. The 35-year-old New Jersey resident clicked on the link included in the message, which took her to a counterfeit eBay site where she entered personal financial information.
Three Worked the Web to Help Terrorists: British Case Reveals How Stolen Credit Card Data Bought Supplies for Operatives July 5, 2007 — The global jihad landed in Linda Spence’s e-mail inbox during the summer of 2003, in the form of a message urging her to verify her eBay account information. The 35-year-old New Jersey resident clicked on the link included in the message, which took her to a counterfeit eBay site where she entered personal financial information.
Scammers Play Robbin Hood to Test Stolen Credit Cards July 6, 2007 — At the ShmooCon hacker conference in Washington, D.C., earlier this year, I had dinner with a guy who worked as an administrator for one of the major 2004 presidential campaign Web sites. Turns out, at one of the busiest periods of the online fundraising period, tens of thousands of small, five-cent donations came into the campaign over the course of several days from a group of computers located in Eastern Europe, with payments being made via thousands of different credit card numbers.
A Word of Caution About Google Calendar July 6, 2007 — I’ve been playing around with Google Calendar, a beta service from the search-engine giant that lets users store — and share — calendar data online. It’s a great Web-based tool, but in experimenting with it I found that far too many people are using Google Calendar without fully understanding how to protect their personal information.
Cyber Crooks Hijack Activities of Large Web-Hosting Firm May 23, 2007 — Organized crime groups have modified a significant share of the Web sites operated by one of the Internet’s largest Web hosting companies to launch cyber attacks against visitors, Security Fix has learned. These servers are home to at least 8,192 active Web sites, most of which appear to belong to individuals and small businesses. According to a Security Fix analysis, more than 2,650 of those sites — or an average of 33 percent of all sites on each server — included computer code designed to silently retrieve malicious software from a variety of online locations.
The Politics of Identity Theft May 9, 2007 — George Fitzgerald never imagined he would take on the nation’s largest financial services industry and win. But his upstart coalition of consumer and business groups did just that when they took up the cause of identity theft victims in Delaware, winning passage last September of a state law enabling residents to opt out of America’s instant-credit economy.
Targeting Spam at the Source: Lawsuit Seeks to Identify Harvesters of E-mail Addresses Apr. 27, 2007 — A company representing Internet users in more than 100 countries filed a federal lawsuit yesterday seeking the identities of people responsible for collecting millions of e-mail addresses on behalf of spammers.
Fortune 500s Unwittingly Become Spammers Mar. 29, 2007 — The next time you receive a piece of junk e-mail touting penny stock, pimping Rolex watches, or lauding a work-at-home scam, consider investigating who really sent it. You may be surprised. Security Fix reviewed spam samples captured in the last month and found many instances of spam sent via computers at well-known Fortune 500 companies.
Enabling the Spammers Mar. 27, 2007 — Spammers are having a field day with a string of recently discovered security vulnerabilities in MailEnable, an e-mail server program offered by many large, dedicated Web hosting companies.
A Fresh Look at Password Thieves Mar. 23, 2007 — Security Fix recently published information about thousands of U.S. residents whose passwords and other data had been stolen by nefarious hackers.Last week, I received more data about the number of victims caused by the hackers’ Trojan horse computer program and more details about the complexity of the attack.
Online Trading Firms Swap Fraud Tips Mar. 22, 2007 — Representatives from some of the nation’s top online stock trading firms will meet with federal law enforcement officials on Friday to discuss ways they can work together to combat Internet fraud.
Cyber Criminals and Their Tools Getting Bolder, More Sophisticated Mar. 14, 2007 — Robert Hoyler thought hackers who broke into his computer stole only his bank account information. But it turned out that the thieves also left something behind: a hidden software virus that recorded his every keystroke. So when Hoyler’s bank issued him new account numbers and passwords, the hackers got all that information, too. His health insurance, online shopping and Social Security data went into a file in a master database at a Web site controlled by the attackers, stashed among personal information on more than 3,220 U.S. residents.
 Tracking the Password Thieves Mar. 14, 2007 — The Washington Post today ran a story I wrote about an epidemic of data theft being fueled by password-stealing viruses and phishing attacks. In some ways, the story behind the reporting that went into the piece is just as interesting, so I’d like to share a few of those details.
Tracking the Password Thieves Mar. 14, 2007 — The Washington Post today ran a story I wrote about an epidemic of data theft being fueled by password-stealing viruses and phishing attacks. In some ways, the story behind the reporting that went into the piece is just as interesting, so I’d like to share a few of those details.
Internet Explorer Unsafe for 284 Days in 2006 Jan. 4, 2007 — Security Fix spent the past several weeks compiling statistics on how long it took some of the major software vendors to issue patches for security flaws in their products. Since Windows is the most-used operating system in the world, it makes sense to lead off with data on Microsoft’s security updates in 2006.
ID Thieves Turn Sights on Smaller Businesses Sept. 28, 2006 — Schuyler Cole needed an accessory for his Palm Treo 600 smartphone, so the Haleiwa, Hawaii, resident fired up his Web browser last month and ran a Google search.After scanning the search results, he purchased the inexpensive item — a USB cable used to synchronize the Treo’s settings with his personal computer — from Cellhut.com, the first online store displayed in the results that looked like it carried the cable. The site featured a “Hackersafe” logo indicating that the site’s security had been verified within the past 24 hours.
‘Shopadmins’ and the ID Theft Cycle Sept. 28, 2006 — washingtonpost.com today published a story based on the 10 hours of lurking I did on a variety of underground chat and Web channels frequented by identity and credit card thieves. From that research, Security Fix confirmed recent data breaches at four online merchants that were unaware that hackers had broken into their databases until we contacted them.
HOPE Speaker Arrested by the Feds July 22, 2006 — NEW YORK, NEW YORK: Security Fix just learned that Steven Rambam, the owner and CEO of Pallorium Inc., a company that bills itself as the largest privately held online investigative service in the United States, was arrested this afternoon by FBI agents just moments before he was to lead a panel discussion on privacy here at the HOPE hacker conference in New York City.
How Many Spams Can a Scammer Scam if a Spammer Can Scam Spams? May 23, 2006 — See if you can say that headline three times fast. I absolutely love the scamming-the-scammer stories because they’re generally so convoluted that they’re almost funny (that is, if you can forget for a moment that there are thousands of victimized consumers involved.)
Blue Security Kicked While It’s Down May 17, 2006 — Hours after anti-spam company Blue Security pulled the plug on its spam-fighting Blue Frog software and service, the spammers whose attack caused the company to wave the white flag have escalated their assault, knocking Blue Security’s farewell message and thousands more Web sites offline.
In Fight Against E-Mail Spam, Goliath Wins Again May 17, 2006 — Eran Reshef had an idea in the battle against spam e-mail that seemed to be working: he fought spam with spam. Today, he’ll give up the fight.
A Time To Patch III: Apple May 1, 2006 — Over the past several months, Security Fix published data showing how long it took Microsoft and Mozilla to issue updates for security flaws. Today, I’d like to present some data I compiled that looks at Apple’s performance on this front.
When Macs Attack Mar. 24, 2006 — A story I wrote this week about “Shadowserver” — a group of security volunteers who hunt down botnet operators online — got picked up by “news-for-nerds” blog Slashdot, and since then a few readers and bloggers have been asking for more details on a botnet I mentioned that was made up entirely of computers powered by Linux and Apple Mac OS X operating systems.
Street-Level Credit Card Fraud Mar. 6, 2006 — Until recently, Las Vegas police officers couldn’t figure out why some of the prostitutes and drug addicts they arrested were found carrying multiple hotel room keys and slot machine player’s club cards. When confronted, the suspects said they kept them as souvenirs or found them on the sidewalk. The cops initially assumed that the cards were stolen, or — in the case of the prostitutes — perhaps belonged to some of their more frequent clients.
Bringing Botnets Out of the Shadows Mar. 21, 2006 — Nicholas Albright’s first foray into some of the darkest alleys of the Internet came in November 2004, shortly after his father committed suicide. About a month following his father’s death, Albright discovered that online criminals had broken into his dad’s personal computer and programmed it to serve as part of a worldwide, distributed network for storing pirated software and movies.
Anti-Spyrus and the Keylogger Connundrum Mar. 16, 2006 — Today we posted a story about the threat from keystroke logging programs and the increasingly sophisticated methods criminals are using to sort through the mountains of stolen password and financial information these eavesdropping devices are phoning home.
Shadowboxing with a Bot Herder Mar. 10, 2006 — Security Fix had an interesting online conversation Tuesday night with a hacker who controls a vast, distributed network of hacked Microsoft Windows computers, also known as a “botnet.”
Botnets: A Global Pandemic Feb. 18, 2006 — Some information security experts say the mainstream Internet security companies have inadvertently yet drastically understated the seriousness and threat posed by the global bot epidemic.
 Invasion of the Computer Snatchers Feb. 16, 2006 — In the six hours between crashing into bed and rolling out of it, the 21-year-old hacker has broken into nearly 2,000 personal computers around the globe. He slept while software he wrote scoured the Internet for vulnerable computers and infected them with viruses that turned them into slaves.Now, with the smoke of his day’s first Marlboro curling across the living room of his parents’ brick rambler, the hacker known online as “0x80” (pronounced X-eighty) plops his wiry frame into a tan, weathered couch, sets his new laptop on the coffee table and punches in a series of commands. At his behest, the commandeered PCs will begin downloading and installing software that will bombard their users with advertisements for pornographic Web sites. After the installation, 0x80 orders the machines to search the Internet for other potential victims.
Invasion of the Computer Snatchers Feb. 16, 2006 — In the six hours between crashing into bed and rolling out of it, the 21-year-old hacker has broken into nearly 2,000 personal computers around the globe. He slept while software he wrote scoured the Internet for vulnerable computers and infected them with viruses that turned them into slaves.Now, with the smoke of his day’s first Marlboro curling across the living room of his parents’ brick rambler, the hacker known online as “0x80” (pronounced X-eighty) plops his wiry frame into a tan, weathered couch, sets his new laptop on the coffee table and punches in a series of commands. At his behest, the commandeered PCs will begin downloading and installing software that will bombard their users with advertisements for pornographic Web sites. After the installation, 0x80 orders the machines to search the Internet for other potential victims.
The New Face of Phishing Feb. 13, 2006 — Phishing is a difficult enough form of fraud to avoid for most computer users, but when some of the biggest names in the financial industry fail to do their part to detect and eliminate these online scams, consumers often are placed in an untenable situation.
A Time to Patch II: Mozilla Feb. 7, 2006 — A few weeks back, Security Fix published figures showing just how long it takes for Microsoft to issue security updates for flaws it learned about through private or public disclosure. I don’t recall receiving as much feedback from readers after any other blog post, and many who wrote in wondered whether we were going to conduct the same analysis for other major software vendors.
 Popular Mechanics: Who’s Stealing Your Identity? Feb. 2006 — THE BUSTS HAD TO BE TIMED TO THE SECOND. Agents from the Secret Service, operating in tandem with law enforcement officials in Canada, Brazil, Poland, Sweden and several other countries, had been investigating the ShadowCrew crime syndicate for months. The agents couldn’t risk giving the cybermobsters time to alert their comrades or delete incriminating data. The group’s Web site, shadowcrew.com, functioned as a sort of identity-theft eBay, a one-stop shop where criminals could buy and sell credit cards, Social Security numbers and mothers’ maiden names like used car parts. Over two years, some 4000 ShadowCrew members had amassed two terabytes’ worth of other people’s lives–18 million e-mail accounts and related personal data–mainly by tricking the victims themselves into giving up their information.
Popular Mechanics: Who’s Stealing Your Identity? Feb. 2006 — THE BUSTS HAD TO BE TIMED TO THE SECOND. Agents from the Secret Service, operating in tandem with law enforcement officials in Canada, Brazil, Poland, Sweden and several other countries, had been investigating the ShadowCrew crime syndicate for months. The agents couldn’t risk giving the cybermobsters time to alert their comrades or delete incriminating data. The group’s Web site, shadowcrew.com, functioned as a sort of identity-theft eBay, a one-stop shop where criminals could buy and sell credit cards, Social Security numbers and mothers’ maiden names like used car parts. Over two years, some 4000 ShadowCrew members had amassed two terabytes’ worth of other people’s lives–18 million e-mail accounts and related personal data–mainly by tricking the victims themselves into giving up their information.
The Long and the Short of Microsoft Patches Jan. 14, 2006 — Microsoft Corp. has often been criticized for taking too long to issue security updates for its software, a shortcoming that critics say leaves customers dangerously exposed to online threats. I recently researched the past three years’ worth of “critical” Microsoft patches — those that mend flaws that hackers can use to take control over Windows computers — and found that while that criticism may still be valid, Microsoft is making progress on a couple of key fronts.
A Timeline of Microsoft Patches Jan. 11, 2006 –A few months back while researching a Microsoft patch from way back in 2003, I began to wonder whether anyone had ever conducted a longitudinal study of Redmond’s patch process to see whether the company was indeed getting more nimble at fixing security problems.
Guidance Software’s Customer Database Compromise Dec. 20, 2005 — Guidance Software — the leading provider of software used to diagnose hacker break-ins — has itself been hacked, resulting in the exposure of financial and personal data connected to thousands of law enforcement officials and network-security professionals.
Conversation with a Worm Author Aug. 29, 2005 –A couple of weeks ago, I wrote about an increasing number of hackers making money by using large groupings of hacked home computers — or “bots” — as massive install bases for spyware and adware, gleaning a commission for each piece of spyware planted on the infected computers.
Black Hat, Day 1: A Cover Up? LAS VEGAS July 27, 2005 — One of the primary reasons companies send their computer security experts to the annual Black Hat security conference here is to learn about new security vulnerabilities that bad guys could use to disrupt Internet communications that most of us rely upon to send e-mail and browse the Web.
Hackers Found Hilton’s Phone an Easy Target May 20, 2005 — The caper had all the necessary ingredients to spark a media firestorm — a beautiful socialite-turned-reality-TV-star, embarrassing photographs and messages, and the personal contact information of several young music and Hollywood celebrities.
Data Thefts My Be Linked: Warrants Service in LexisNexis Account Breach May 20, 2005 — A computer break-in at database giant LexisNexis Group may be linked to members of a group of young hackers involved in the theft of revealing photos and celebrity contact numbers from the cell phone of hotel heiress Paris Hilton, a senior federal law enforcement official said.
When Phones Lie May 19, 2005 — I’ve spent the last few months reporting a couple of stories on the hacking of hotel heiress Paris Hilton’s cell phone and the escalating investigation into the January intrusion at LexisNexis, in which hackers hijacked several accounts to download private information on thousands of consumers. Turns out the attacks were done by the same group, according to my reporting.



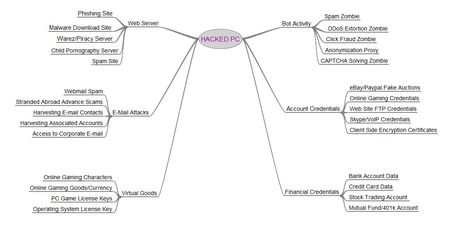



Nice job on the new site Brian. I’ve added you to my blogroll. Thanks for all the great information.