One of the more common questions I hear from readers with computer virus infections is, “How do I get rid of a virus if I can’t even boot up into Windows to run an anti-virus scan?” Fortunately, there are a number of free, relatively easy-to-use tools that can help on this front.
The tools in this review are known as a “rescue CDs.” These are all free, Linux-based operating systems that one can download and burn to a CD-Rom. Once you’ve configured your PC to boot from the CD you’ve just burned, you can use the CD to scan your hard drive, and — depending on the type of rescue CD you choose — even copy files to a removable drive.
 I have recommended more full-fledged versions of these rescue CDs (also known as “Live CDs) as a way for small businesses to protect their online banking sessions from malicious software, the lion’s share of which simply fail to run on non-Windows-based operating systems. But several anti-virus companies also offer slimmed-down Linux-based rescue CDs that can be extremely handy in getting rid of a persistent malware infection, or just for getting a second opinion (or third or fourth) about the state of your system.
I have recommended more full-fledged versions of these rescue CDs (also known as “Live CDs) as a way for small businesses to protect their online banking sessions from malicious software, the lion’s share of which simply fail to run on non-Windows-based operating systems. But several anti-virus companies also offer slimmed-down Linux-based rescue CDs that can be extremely handy in getting rid of a persistent malware infection, or just for getting a second opinion (or third or fourth) about the state of your system.
Before I go any further, let me just state for the record that I don’t believe there is any substitute for having known good, solid backups of your data and your entire hard drive to restore to in case things go south. I also urge users to segment their systems so that important data files are on a separate chunk of hard drive space than the Windows operating system, which tends to make restoring backups a far simpler affair. I’ll post a separate tutorial on setting up a good backup plan soon. For now, though, I want to introduce readers to these simple tools.
Just one housekeeping note before I get started: If you want to run a rescue CD on a laptop, you’ll need to plug the notebook into a router or other Internet connection via a networking cable. The reason is that the first thing you’ll need to do when you boot into the rescue CD is update the program’s anti-virus definitions, and that requires a working Internet connection. I don’t believe any of these tools support wireless networking, but in any case setting that up is far beyond the scope and ambition of this brief how-to.
Grab the CD image
Several anti-virus vendors offer burnable rescue CDs that are based on Linux, including:
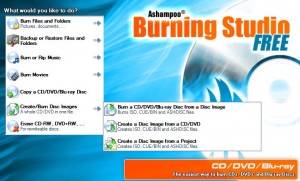
After you’ve download the file, burn the image to CD-Rom or DVD. If you don’t know how to burn an image file to CD or don’t know whether you have a program to do so, download something like Ashampoo Burning Studio Free. Once you’ve installed it, start the program and select “create/burn disc images,” and then “burn ISO.” Locate the .iso file you just downloaded, and follow the prompts to burn the image to the disc.
Incidentally, if your computer is a netbook and doesn’t have a CD-Rom drive — or if you’d just prefer to boot the rescue disc from a USB drive — you can create a bootable USB/flash drive using the same .iso image by downloading and running this free tool here.
Set your PC to boot from the CD
When the burn is complete, just keep the disc in the drive. We next need to make sure that the computer knows to look to the CD drive first for a bootable operating system before it checks the hard drive, otherwise this rescue will never be recognized by the computer. When you start up your PC, take note of the text that flashes on the screen, and look for something that says “Press [some key] to enter setup” or “Press [some key] to enter startup.” Usually, the key you want will be F2, or the Delete or Escape (Esc) key.
When you figure out what key you need to press, press it repeatedly until the system BIOS screen is displayed. Your mouse will not work here, so you’ll need to rely on your keyboard. Look at the menu options at the top of the screen, and you should notice a menu named “Boot”. Hit the “right arrow” key until you’ve reached that screen listing your bootable devices. What you want to do here is move the CD-Rom/DVD Drive to the top of the list. Do this by selecting the down-arrow key until the CD-Rom option is highlighted, and the press the “+” key on your keyboard until the CD-Rom option is at the top. Then hit the F10 key, and confirm “yes” when asked if you want to save changes and exit, and the computer should reboot. If you’d done this step correctly, the computer should detect the CD image you just burned as a bootable operating system. [Unless you know what you’re doing here, it’s important not to make any other changes in the BIOS settings. If you accidentally do make a change that you want to undo, hit F10, and select the option “Exit without saving changes.” The computer will reboot, and you can try this step again.]
Note that if you chose above to create a bootable USB drive instead of a rescue CD, you will need to tell your BIOS to select the USB drive as the primary startup target.
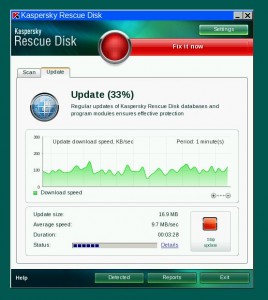
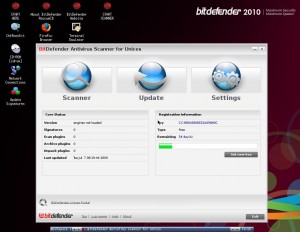 Scan and remove any found malware
Scan and remove any found malware
Some of the free rescue CDs above are more intuitive and user-friendly than others. Of them all, I thought Kaspersky and BitDefender offered the easiest to use and probably the most newbie-friendly interfaces. Both boot into a desktop-like environment that may be more familiar to Windows users. In addition, they each offer an Explorer-like window that allows users to examine files on the Windows hard disk. BitDefender’s rescue CD was the only one I tried that had a copy of the Firefox Web browser built into it. It also includes a point-and-click program that checks for common rootkits, tools often planted on hacked machines to hide the presence of malicious software.
If you have a secondary USB drive connected to the machine, you may even be able to use either the Kaspersky or BitDefender rescue CDs to copy files over to the external drive, although moving files from a damaged hard drive to a backup drive is probably best accomplished with an all-purpose type of Live CD, such as Ubuntu or Knoppix, which generally have better support for removable drives.
It is safe to power off the PC when you’re done with these rescue CDs. Just make sure to remove the CD before you try to boot up again into Windows, otherwise the computer will boot back into the rescue CD.




Dang, you should have posted this Friday, I needed it Sat night… 🙂
Thanks!
I use Windows PE: it requires me to load and edit the Registry hives manually, but it never goes out of date.
I have several LiveCDs that I use, and the one I use most frequently is BartPE. For the same reason – I can mount registry hives and correct registry errors that may be preventing bootups.
There is one other option of course. You can remove the hard drive from the infected machine, and put it in a USB enclosure. Then you can plug it into a clean machine (making sure that you don’t have autorun turned on), and scan the disk that way.
I can make one other observation – one of the Linux-based LiveCDs that I used corrupted the disk in a horrible way. Fortunately I did a complete backup before attempting the cleanup so I could restore to the infected state and then use a different tool.
Fortunately I haven’t had to use any of these tools for months now.
Excellent resources, Brian. It’s been 3 months since you left WaPo and I didn’t realize how much impact your blog had on my ability to be in-the-know. I relied on you for timely accurate information on important information security topics. I’ve been struggling to find other sources with the same quality I became so accustomed to. I’m glad I found your personal blog. I’ve got you back in my RSS feeds now. Keep up the great work!
Royce Renteria
Doug, I’m another fan of yours who finally succombed to the e-mail notices as a way of keeping ‘Brian aware’. You’ve been a big help to me in the past, and I didn’t want to miss a post!
About these CDs, I can burn CDs to my laptop, which is connected to the internet by dial-up. (We cannot have an external modem due to the gassing off and our allergies/eye condition.)
So with that connection, could I use one of those CDs to restore my OS should it be shut down? I didn’t understand the laptop limitation that you mentioned with needing wireless.
Hi Jane,
It is unlikely that any of these rescue CDs will work with dial-up connections. The reason is that you need a special set of programs and connection scripts to dial out to an internet connection using Live CDs, and that’s almost certainly not included in these rescue CDs. Sorry.
I don’t know if you caught my comment below Brian, but Puppy Linux does have dialup capablities, and you can even use your smartphone via USB if needed.
While the following comment may not apply directly to the problem of unbootable windows systems, don’t forget to TURN OFF the windows file protection (WFP) feature prior to running antivirus protection from live cds.
Malware often rely on WFP to resurrect themselves. If WFP is not turned off you may find that the malware successfully restores itself even if the hard disk is successfully cleaned by these live CDs.
For serious propeller-heads, there are even better rescue CDs available, though I realize you are aiming here at a different user population. Also, there may be other reasons why you did not mention, for example, **HiRen’s Boot CD** but intrepid malware slayers may find themselves a mere google away from industrial strength tools they will instantly assign to their “cold dead fingers” category (as in, when they die, the CD will have to be pried from same).
Hirens is a great tool, used it hundreds of times for various reasons. Probably not a tool for my parents… but for those more into “nerd talk” as my parents call it, its a great resource as well.
Great article overall!
Hiren’s is great if you are a CROOK! Why mention warez projects?
Brian,
Follower of your chat and blogs from WaPo.
What are good tools for backing up the computers?
I do have 4 computers and what is best way of backing them up.
For windows users, Cobian backup is free and easy. For linux users, rdiff-backup or rsync scripts work quite well.
Depends on what sort of backups. Full system? Large removable hard drive, and Norton Ghost.
Just the data? Removable hard drive, or high capacity USB key, and XCOPY. No, really, it’s great for incrementals. Use a batch file.
I have a Mac and use Time Machine, plus copying the vital data to a removable hard drive. HD is kept (rotated, actually) in the safe deposit box at the bank.
I like SyncBack SE from 2BrightSparks. Powerful, yet simple. It schedules incremental file-copy style backups to a removable or internal HDD. I use it for my SBS server as well for company files. Not Exchange-aware, I use NTBackup for that (to the same disk).
I use laptop HDDs with cases, swap weekly, and always carry one with me in my backpack. I’ve found that laptop HDDs tend to be more suited to travel, which is perfect for me. I also like the way it emails me the results of the backup.
This way, I always have all my files with me. It’s a good feeling.
I sugest you look up easeus free backup 2 includes rescue CD.iso so that you can restore a computer from apreviously made backup.
This is a great article I plan on passing along to my less technical family member whose computers I normally fix.
For your list:
Sophos: http://www.sophos.com/support/knowledgebase/article/52011.html
At the risk of being modded into hell, I would argue to just go all the way with a Linux live CD. If your needs are basic web browsing, e-mail, occasional chatting, and word processing, there is really no reason to stick with Windows and put up with the constant malware threats.
I have to shake my head with every story BK puts out about another business getting ripped off tens to hundreds of thousands of dollars or Microsoft scrambling to contain another 0-day because of Windows insecurity.
The people I have converted over to Ubuntu? Aside from an occasional HOWTO question, I haven’t been called back to help fix something.
And yes, separating your data from the OS is really the only way to go. If you blow away your OS it can be reinstalled and tweaked in a few hours. Your data? It might take years, if ever, to get back the irreplaceable. (You do backup, don’t you? And test your backups?)
Stop wasting your time thinking that Windows will ever be secure because it won’t be. Not until Microsoft wakes up and starts over from a clean slate. But they won’t because they will have to sacrifice backwards compatibility and their dominance from keeping everyone on the upgrade gravy train. They will keep promising security and fail to deliver as they always have been.
I agree with AlphaMack in creating a separate partition for the data files.
We always took that one step further in creating a separate partition for the temp, IE temp and pagefile. This would ONLY be formatted in FAT32 so no transaction logging could occur as well.
I tried Ubuntu as recommended in a previous column, but could not boot from it. I’ve forgotten the details now, but I learned that Ubuntu will not work with a driver my system requires for boot access. I was surprised, because my computer is a very typical IBM (pre-Lenovo). I wonder if I would be successful with another type of LiveCD, but it took almost 2 hours to try (and then unsuccessfully troubleshoot) Ubuntu. Trial and error could be exacerbating.
A few notes on the rescue CDs:
* The Avira CD is updated daily with new virus signatures, so it doesn’t need to download updates and can be run well even on laptops with only wireless connections. It can also download updates, but if you’re using a recent-enough CD then that’s not a requirement. It can be downloaded as either an ISO that you burn yourself or as an EXE that will handle the CD burning for you.
* F-Secure’s CD can work with a virus definition file loaded from a USB key, but you’ll need to track that down, download it, and put it on a key as well as burning the CD.
* Dialup won’t work well for most because the virus signature updates are frequently 50-80 MB, so at download speeds you’re looking at 2-4 hours to download the updates and that’s assuming that the download goes smoothly.
* SARDU (google it) is a VERY handy tool for combining multiple rescue and utility CDs into a single ISO for burning to a CD or DVD. It also handles USB drives. I believe the beta of 1.0.7.2 is able to download virus definition updates for Avira and F-Secure.
* If you have an infected system and a “Live” CD but no antivirus/rescue CD, you may be able to do some initial cleaning by booting from the CD and following a few housekeeping steps:
– Delete the Content.IE5 directory from each user. On XP they’re in a hidden directory under “C:\Documents and Settings\(username)\Local Settings\Temporary Internet Files\Content.IE5”, in Vista and Windows 7 they’re in “C:\Users\(username)\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5”. Deleting these directories from a live CD will simply wipe out the files that Internet Explorer has saved to speed up returning to some web sites; the directories will be recreated automatically. They’re well hidden by Windows, but they’re there.
– Empty out the Temp directories also found under C:\Documents and Settings\(username)\Local Settings\Temp or C:\Users\(username)\AppData\Temp – you can delete files or just create a new folder in that Temp folder (e.g. Temp\New Folder) and move everything into it. This may block infections that are in the Temp folder.
– Do the same thing with C:\Windows\Temp directory (move files to a subdirectory rather than just deleting, just in case)
– Look in C:\Windows\System32, sort by date and look for files created within the last day or two. Don’t delete anything, but if you see something suspicious you can rename it (e.g. from “iamavirus.exe” to “iamavirus.exe.disabled”). Most of the files in this directory are required for Windows to work, so don’t delete anything – you might be wrong about the file and need to put it back.
– Look in C:\Program Files for directories created within the past day or two, particularly if they have only a single .exe file within them. If you find one, rename the directory or .exe to include something like -disabled at the end of it.
Sorry, but I simply do not agree. We should NOT be trying to “remove” malware. That era is long gone. The methods we used then have been surpassed. Doing the same old things–even in new ways–is just fooling ourselves.
Clearly, strong differences still exist over “removing” malware from Microsoft Windows. However, based on my research, analysis, and experience, I view working to “remove” modern malware as a serious mistake.
Malware “removal” was something we did years ago, before rootkits and bots. Nowadays, the removal option has been taken from us. If we need a system which is guaranteed clean, we must re-install the OS (or perhaps recover an uninfected image). And in exactly what way could a system which is not guaranteed clean possibly be a satisfactory result?
Modern bots are not like old-time viri. Bots call home on broadband, then take orders and download code from the botmaster. Some bots seem to download a range of malware friends, apparently as a distraction. Removing a distraction is not a victory, it is a defeat. Bots also modify the system beyond their own files, and no scanner will expose what the bot has done. Thinking we have restored a system just by removing malware files is another defeat. And since there currently exists no tool which can certify a computer as “clean,” we cannot rightfully claim that we have accomplished anything at all.
I am not alone in these views:
http://www.baselinemag.com/c/a/Intelligence/Microsoft-Says-Recovery-from-Malware-Becoming-Impossible/
“When you are dealing with rootkits and some advanced spyware programs, the only solution is to rebuild from scratch.”
http://forums.techarena.in/security-virus/989265.htm
“The best current practice for cleaning up a system on which malware has been executed is to reinstall the operating system cleanly.”
https://www4.uwm.edu/itsecurity/news/news/virus_recovery.cfm
“Complete reinstallation is usually necessary:”
http://www.infoworld.com/d/security-central/starting-scratch-only-malware-cure-451
“If you discover malware on your system, don’t mess around. Back up your data, format your hard drive, and begin again.”
http://ask-leo.com/how_do_i_remove_a_virus.html
“The only way to be absolutely positive that you’ve removed any and all viruses is:
* Backup
* Reformat
* Reinstall
* Update
* Restore
* Learn.”
Reinstalling Microsoft Windows is not trivial. It is not fun to lose most configuration information and reinstall application programs. This is sad, but it is the reality we have. Claiming that we can remove malware will not protect us; instead, it will set us up for the kill.
Terry,
I’m sure Microsoft would *love* for the default response to malware removal be a reinstall. Why? So many people don’t have their install CDs *or* in this day and age of online downloads, their keys to Ms Office. I’ve had multiple clients who bought Office legally, had to reinstall, but couldn’t find their key or if they had it, find the ‘right’ Office installer to reinstall with the key they had. MS completely unhelpful in that regard. When told they had to pay another $400 for MS Office Small Biz or whatever, they were NOT happy.
A skilled professional can clean MOST machines out there without a reinstall with a solid chance of not being reinfected or leaving anything it shouldn’t. No, it’s not fool proof and there is always a risk. But when I turn a cleaned PC back over to a client, I know they are MUCH more likely to be reinfected via IE and bad user practices than some well hidden timebomb. Yet the client is happy because you return their computer in the state they remember it and it works.
Ethically, I inform all my clients about monitoring bank statements, changing passwords, and so on and will also tell them there is no way to be 100% sure everything was found, but the chances of a residual infection are slim and that reinstallation is an option. None have chosen it and I’ve only had to wipe/reinstall probably 1% of the infected machines I’ve seen.
So in an ideal world, we’d wipe and reinstall – but realistically? Just not happening until data, settings, AND APPLICATIONS are modular enough to be backed up and restored. But then you risk transferring the infection to the new machine. And given how often I’ve seen residual exe files stored in My Documents or other commonly transferred sections a wipe and reinstall is STILL susceptible to reinfection.
Hi Mike!
“I’m sure Microsoft would *love* for the default response to malware removal be a reinstall.”
We do know that Microsoft’s goals are not our goals, for if they were, we would have a better malware response. Software consumers at all levels need to be aware of the reinstall problem and be sure to acquire and save the install media.
When I reinstall XP (for friends and family), I partition the drive into system and data. I was using 30GB for C:, although Win7 appears to want 40GB (!), so I guess that will be standard. The goal is for all system stuff to be on C:. So I image and recover C: for malware, and D: for edit files. I hope that Windows does not reach out to D: to run files (although the user might force that).
All this is so much work that I am pushing everyone to Puppy Linux on DVD for browsing. Other than needing special Windows printer drivers, browsing is mostly what they do, and they can do that on Puppy.
“A skilled professional can clean MOST machines out there without a reinstall with a solid chance of not being reinfected or leaving anything it shouldn’t. No, it’s not fool proof and there is always a risk.”
With the hope of not offending, I have to ask how you know the machine is clean: If the bot hides really well, we will think it gone when it is not. Thinking there is a low probability of a bot hiding implies that we know when it does hide, but that is just what we cannot know, for if we did, we would get it. We cannot get what we cannot see.
If the bot changes some part of the OS not normally checked (e.g., hosts file), or is dynamic (e.g., the registry), or who knows what, that may not be found and so stays changed. Microsoft has seemingly endless ways of starting hidden malware.
“I know they are MUCH more likely to be reinfected via IE and bad user practices than some well hidden timebomb.”
I think we need to be using Firefox with security add-ons. That can be initially strange for users, but the problems are what they are, and ignoring them is not going to help. Maybe we need a special class of operator, like elevators used to have.
Again, this issue of saying “more likely” implies knowing the probabilities for both options. But it is impossible to know the probability of a bot escaping detection, because if we knew of such a bot, we would get it. In the end, as far as we know, there is no bot. But there is some probability of a hiding bot nevertheless. Until we know that probability, we cannot compare it.
“And given how often I’ve seen residual exe files stored in My Documents or other commonly transferred sections a wipe and reinstall is STILL susceptible to reinfection.”
Then I would argue that we need better practices to guarantee stopping malware. I think we cannot hope to keep up with multiple teams of malware kit programmers and all their buyers. Our only hope is to start new again and try to keep clean.
Thanks for your comment.
Re: user-friendly Linux Live-CDs for moving data back and forth: Look at Puppy Linux. The Drive Mount util is simple to use for a beginner and you can mount any device you have connected or connect while running. You have a CD/DVD/Blue Ray burner and you can remove the Puppy CD after boot due to Puppy copying itself to RAM.
It also has wireless scanner, DHCP or manual config for the NIC or wireless, Samba scanner, etc., etc., etc..
You also have a full complement of disk tools, and the CD image is only 115MB.
Re: Needing to use a dialup service with a Live CD: Puppy does this also.
@Alan Miller:
One important ‘hiding place’ of malware that you are missing is {drive}:\System Volume Information
You will find this directory on all partitions and have full access to it if you boot from a Linux Live CD such as Puppy mentioned above.
True, but I’ve never needed to remove anything manually from System Volume Info so I’m not familiar with how often the contents get updated. For the most part contents don’t change that often in Program Files and System32.
My general take is that the only time to do manual cleaning (beyond emptying the assorted temp files to speed up scanning) is if you have no other choice – it’s something of a Hail Mary attempt to get the system back to a spot where you’re able to run actual anti-malware/anti-virus tools on it.
Even then, you may find yourself with headaches that can only be cleaned up with registry fixes, such as “XP AntiSpyware 2010” and “XP Antivirus Pro 2010” based on this article: http://www.myantispyware.com/2010/02/22/how-to-remove-xp-antispyware-2010-xp-antivirus-pro-2010/
Basic summary, one of the things these programs do is change how .exe files are launched by Windows Explorer by updating the file associations.
Very true Alan. So once you’ve found what program is being run in the guise of the exe file you wan to run, or if you have experience and can spot added files that don’t belong, you can boot with a Linux Live CD and erase those files. I simply use Puppy Linux because it so bloody small and yet so loaded with simple tools.
I ran a computer network service company, and many times we found the culprit in the System Volume Info dir when we pulled the drive out and scanned it with another computer, though you still can’t get in there if the other computer is running Windows — but luckily Linux is another story.
Using a combo of these tools, our average percentage of getting a system back online without a reinstall was approx 97% in 19 years (with 1800+ clients in my database at the end.)
Agree with the ‘Combination of Tools’ statement. Clients may not like having to wait longer to get their system back BUT it’s worth it. ComboFix, SuperAntiSpyWare, Security Essentials, Malware Bytes, SpyBot, Live CDs, and others can find a LOT of stuff. And beyond the well known ‘no tool finds everything’ another is ‘One tool’s idea of a fix is another tools idea of lazy’ I’ve found ComboFix and SpyBot cleanup a LOT of residual stuff that other tools leave behind (may only turf the executables) Yes – nothing finds everything, but tools can reduce the amount of manual exploration and fixing you have to do on a badly infected machine.
You can scan and delete files in the System Volume Information folder when the drive is mounted as a secondary on a XP Pro test machine. Just take ownership of the folder.
This also works if the user set his My Documents folder to be secure when settings the password.
I’ll put in a plug for Windows SteadyState and Deep Freeze. Never a virus issue when setup correctly.
@Tom Seaview:
Putting a drive inside a USB enclosure is a too much trouble. There are adapters that will allow you to simply plug in to the power and data ports on any size/format of drive and go directly from that into your USB port. Much quicker.
I agree with the point about hard drive enclosures. Many are flimsy — apparently we’re not supposed to swap out the drive more than two or three times. Many overheat.
For $40 you can get a “universal” hard drive adapter without an enclosure box. Plug it all together when you need it; take it apart and store it when you don’t.
Hi .
Iuse A.V.G full paid version.
I dont have any problems.
Rm
I use ESET Nod32. I keep all my Windows updates current w/auto update turned on, and I have never had a problem with a virus or with spam. With all the information and warnings that Brian has posted over the years I, for the life of me, do not understand how people get viruses. It is like people read but do not understand or do not care.
Perplexed!!
Several commenters suggested mounting the infected drive in a known clean computer. This is very rash.
Whether you mount it as a slave on an IDE ribbon, or in a SATA or eSATA port, or on a USB hard-drive adapter or enclosure, Windows will see it as a drive and mount all the partitions. Some viruses will copy themselves to any partition on the machine.
A couple of weeks ago, a client brought in an infected computer. I used a USB flash drive to install an antivirus (client’s computer didn’t have one). My flash drive got infected. My attempts to clean the drive by using a newly refurbished computer failed, and the computer got infected.
I succeeded in reformatting the flash drive on yet another refurbished computer worked, but that computer also got infected!
Morals:
* Never connect in infected drive or computer to anything you can’t easily replace or fix.
* Unplug infected computers from your LAN immediately. Disable WiFi (there may be a switch on a laptop — unscrew the antenna and remove the WiFi card on a desktop).
* If you need to download something or consult the Internet, use a healthy machine.
* Always use a finalized CD or DVD to transfer files to an infected computer.
* Always use a blank CD or DVD to copy files from an infected computer, but you can still inadvertently copy malware to it.
We have given up trying to disinfect our clients’ computers. Just replace the computer. It is much faster, and as mentioned above, it is the only safe method. (We wipe and refurbish the infected box.)
You can also use a USB flash drive with a write protect switch. These have gotten rare in the past few years but there are still a few out there. I know of two maintained lists – mine at List of USB Flash Drives with Hardware Write Protection Switch and the c’t Magazin FAQ in German (but works well with Google’s translations).
We use a single slot SD Flash to USB adapter. Most SD cards still have a R/W switch, making it trivial to do. We have a bunch of these and a standard ‘tool’ image we burn to the flash card, then lock it read only
http://goo.gl/fTw2
Works great. The unit is a little wide so we’ve occasionally encountered a USB slot where it wouldn’t fit – but a short USB extension cable does the trick (or a KVM with built in sharable USB slots – even better)
Be careful with SD card adapters – the write protection on them is more of a request to the operating system to mount the drive read-only. The write protect switch on those cards does not have any connection to the inside of the card, it’s just something that’s read by the card enclosure and some cheaper ones have been known to ignore it or read it incorrectly.
Brian, you might mention that a live CD could be the only way even if the machine boots.
Every week or two I see an infected machine with no antivirus. Presumably the malware removed or disabled the antivirus.
Even if the antivirus is still there, it may have been turned off by the malware, which then blocks access to dozens of security sites on the Internet.
If you are having issues running virus scanners whilst
your computer is turned on, try to start into ‘Safe Mode’.
If you’re using a version of Windows, you’ll be able to do
this. (Windows XP, Windows Vista & Windows 7)
Safe Mode:
Turn computer off
Turn computer on whilst tapping F8. When prompted select
‘safe mode with networking’
When prompted, click Yes & start into Windows as normal.
Hey, hopefully someone can make use of this 🙂
If you are having issues running virus scanners whilst your computer is turned on, try to start into ‘Safe Mode’.
If you’re using a version of Windows, you’ll be able to do this. (Windows XP, Windows Vista & Windows 7)
Safe Mode:
Turn computer off
Turn computer on whilst tapping F8. When prompted select ‘safe mode with networking’
When prompted, click Yes & start into Windows as normal.
Sometimes the only way to get rid of the viruses is the oldstyle method , Full Format HDD.
As a anti-virus could remove some of the viruses and not all format is the safest method.
And also in order to keep and save at least some of your files you should use a backup software , a free backup software is http://www.dmailer.com/dmailer-backup.html , it has a lot of features and you will also be able to store the backup online on their servers.