When you’re lurking in the computer crime underground, it pays to watch your back and to keep your BS meter set to ‘maximum.’ But when you’ve gained access to an elite black market section of a closely guarded crime forum to which very few have access, it’s easy to let your guard down. That’s what I did earlier this year, and it caused me to chase a false story. This blog post aims to set the record straight on that front, and to offer a cautionary (and possibly entertaining) tale to other would-be cybersleuths.
 On Jan. 16, 2013, I published a post titled, “New Java Exploit Fetches $5,000 Per Buyer.” The details in that story came from a sales thread posted to an exclusive subforum of Darkode.com, a secretive underground community that has long served as a bazaar for all manner of cybercriminal wares, including exploit kits, spam services, ransomware programs, and stealthy botnets. I’ve maintained a presence on this forum off and on (mostly on) for the past three years, in large part because Darkode has been a reliable place to find information about zero-days, or highly valuable threats that exploit previously unknown vulnerabilities in software — threats that are shared or used by attackers before the developer of the target software knows about the vulnerability.
On Jan. 16, 2013, I published a post titled, “New Java Exploit Fetches $5,000 Per Buyer.” The details in that story came from a sales thread posted to an exclusive subforum of Darkode.com, a secretive underground community that has long served as a bazaar for all manner of cybercriminal wares, including exploit kits, spam services, ransomware programs, and stealthy botnets. I’ve maintained a presence on this forum off and on (mostly on) for the past three years, in large part because Darkode has been a reliable place to find information about zero-days, or highly valuable threats that exploit previously unknown vulnerabilities in software — threats that are shared or used by attackers before the developer of the target software knows about the vulnerability.
I had previously broken several other stories about zero-day exploits for sale on Darkode that later showed up “in-the-wild” and confirmed by the affected vendors, and this sales thread was posted by one of the forum’s most trusted members. The sales thread also was created during a time in which Java’s maker Oracle Corp. was struggling with multiple zero-days in Java.
What I didn’t know at the time was that this particular sales thread was little more than a carefully laid trap by the Darkode administrators to discover which accounts I was using to lurk on their forum. Ironically, I recently learned of this snare after white/grey hat hackers compromised virtually all of the administrator accounts and private messages on Darkode.
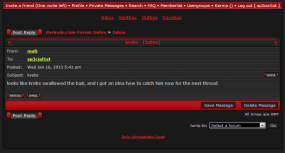
“Looks like Krebs swallowed the bait, and i got an idea how to catch him now for the next thread,” wrote Darkode administrator “Mafi” in a Jan. 16 private message to a co-admin who uses the nickname “sp3cial1st”.
Following this post, the administrators compared notes as to which users had viewed the fake Java zero-day sales thread during the brief, two-day period it was live on a restricted portion of Darkode. “I have taken a careful examination of the logs related to the java 0day thread,” sp3cial1st wrote to a Darkode administrator who used the nick “187”.
A side note is probably in order here. This 187 user was apparently quite paranoid; he changed nicknames on the forum like so many pairs of underwear. In this screenshot of a private message between 187 and sp3cial1st, we can see 187 asking to have his forum name changed from his previous nick — “teardrop” — to 187. This is interesting because “teardrop” was the nickname used by the Darkode member who bragged to other admins about having his friend launch a distributed denial-of-service attack on my site on July 10, 2012, after I wrote about a zero-day exploit in Plesk that I’d discovered for sale on Darkode. By the way, 187 appears to be a Canadian citizen who likes to use the alias “Ryan Russels”; by his own admission, 187 is a 36-year-old male currently living with his wife in Dubai and wanted in Canada for unspecified criminal charges.
At any rate, leaked private forum messages indicate that the administration of Darkode came up with the fake Java 0day idea after determining that their clever watermarking scheme had been exposed. Forum admin Mafi devised a system for secretly tagging each Web page on the forum with unique markers that could help identify and then ban forum accounts that were being used by security researchers to take screen grabs.
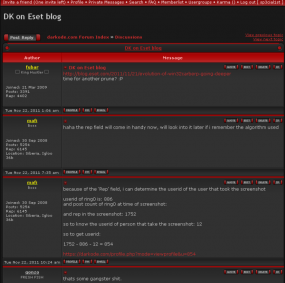
Mafi’s watermarking system can extract the user ID used to take any screen grab as long as that image includes the information under the “Author” sidebar on the left edge of the forum page: As explained in the screen shot to the left, the watermarking system computes two qualities present in that area: the “rep” or reputation field, and the user’s number of posts.
I debated whether to run this post detailing how I got fooled by Darkode’s disinformation campaign/mole hunt, in part because I worried that explaining it all could entail “outing” some of my sources and methods. But I believe that one only grows by admitting one’s mistakes, and so to Oracle and to any readers I may have upset or misled by my previous story on this apparently bogus zero-day, I heartily apologize.
Incidentally, these screen shots are hardly the full story. Earlier this week, a security blogger that I’ve long included on my blogroll — Xylitol — leaked a huge archive of screen shots he’s taken from his own lurkings on Darkode. Those, combined with the dozen or so administrator account screen grabs in this post, offer hours of fun for any researcher interested in profiling the most active members of this forum.
For example, looking at the personal signature used by one of the Darkode admins — a user with the screen name “Parabola” — we can see that this user owns several shady businesses, including a service that helps users move money between virtual currencies such as WebMoney and Liberty Reserve. Looking closer at that service, one can discover that the same server also hosts spamming and keylogging services. According to his introductory post to Darkode when he joined in 2009, Parabola work(ed/s) in IT at a software company based in Texas.
Closer inspection of the screen grab of Parabola’s intro shows that he was invited to Darkode by a user named Iserdo, the former owner of the forum. This latter identity belonged to a hacker arrested in 2010 under suspicion of creating, selling and maintaining the “Mariposa” or “Butterfly” botnet, a crime machine that infected millions of PCs. Other active Darkode members that have been busted by authorities for botnet activity include BX1, a 24-year-old Algerian national who was recently arrested in Bangkok for allegedly earning millions of dollars by operating botnets powered by the ZeuS Trojan. Interestingly, BX1 himself warned other Darkode members in November 2012 that the FBI was investigating him. A portion of the Darkode community’s reaction to his arrest can be read here and here.



One word for DK guys “Pwned”
xD
Awesome post )
“That’s some Gangsta Shit!”
I run a (public) forum and the idea of digital watermarking like that came to me a few times when we were suffering leaks from the administration forum.
Unless you have two accounts/setups you can check (to verify that information isn’t changing based on that), you could theoretically embed it into anything. Add a flag to text that changes based on your username, appends something to a link… There are a lot of options.
It isn’t too surprising that you were caught with this method, though. 🙂 It’s hard to detect, but it seems obvious in hindsight.
Brian, do you use a VM when you visit those sites to avoid being compromised?
Hi Rey,
I use multiple VMs for just about everything I do that touches the Interwebs, both regular usage and in underground. It’s just too risky otherwise for what I do.
That makes sense. It was the first question that popped into my mind when you wrote that you were lurking on there.
And being transparent in this post was the best route IMO.
Can you explain VMs and how best to utilize them for the Interwebs?
In your comments you say that you use several VMs for anything to do with the internet, i would love to learn more about that. What sort of setup do you use or if thats to personal(or a security risk) then what sort of setup do you feel would be the most secure without demanding deep knowledge in infosec. Or in other words what do you deem best practice in using VMs for security. Or any relevant links would be great!
I’ll give this some thought. It’s definitely a post worth pursuing, it’s just one that might be technically tricky to get across simply to the Average Joe/Jane. But I’ve done it before with Live CD instructions, so this shouldn’t be too much more difficult. Thanks for the idea.
But is your site really meant for average Joes? Sure, we get a few in here once in a while, but more than that we either have regulars or the odd angry person you’ve PO’d. Never hold back, but keep a balance is all. We should all share what our arsenal is so we can all better ourselves and learn.
And get a detective hat, damn it!
While it’s true that the vast majority of people who REPLY to his articles are like this, I strongly suspect that for Brian to achieve any sort of income he’d have to vastly exceed only this small majority, even with advertising.
This said, I am now kind of curious what sort of traffic/pagehits you get Brian — I assume you mostly get US readers but have you studied, for example, the percentage of laymen versus technical professionals read your pages in any way? And do you use those metrics to guide you in what to write and how often?
Thanks for any reply. 🙂
I meant this small minority, not small majority. Sorry. Not my first language. 🙂
I meant small minority, not small majority. Sorry. This is not my first language. 🙂
Voksalna, the information you’re seeking (some of it) is not hard to find. It is at the top of my blog, under the “Blog advertising” tab.
http://krebsonsecurity.com/cpm/
Rich & Griff are spot on. Please do a post on that. I’d love to do some poking around myself…in a safe way. 🙂
I guess you could start by downloading VirtualBox from Oracle (free download). You essentially create a VM along with a new virtual disk. You tell it how much memory to assign to the thing, and what types of virtual devices are to be a part of the virtual machine.
Finally you point the virtual DVD drive to point at something like a Linux install iso image, and turn on the VM. It is almost like just doing a clean install of Linux on a clean machine. That by itself is really most of it.
The main other thing that you might wish to do after having installed Linux is install the “VBoxGuestAdditions” package which will mainly help to improve performance. This is something that comes with VirtualBox – you just change the DVD drive and point it at the guest additions iso.
That’s just a starting point, really. You can use it to play around and get used to how it all works. If you are going to mess about with sites that distribute malware, you ought to read about taking machine snapshots first so you can roll the thing back if the machine gets infected with something.
think a vm gives complete security? Years ago I used a snapshotted vm running on vista. V ista had the tcpip stack pulled… the vm used bridging. It still got compromoised afters two weeks online heavily downloading. I think I know how ..
Brian your just like me , cover thou 6 o’clock at all times . 🙂
sorry your like buttons aren’t working. Big like to this story. Thanks for sharing 🙂
Even on Tor sites I’d think most operate not thinking people aren’t lurking their stuff, but not caring that they do. When does this “Secret club of cool kids” ever work?
“When does this “Secret club of cool kids” ever work?”
Three can keep a secret, if two of them are dead.
It works when all users hide any and all aspects of their true identities from each other which means there’s nothing to use when trying to identify them. You’re not going to hear much about the groups that aren’t busted are you.
AFAIK Tor still does this pretty well provided people make no link to their real life identity and follow. appropriate security precautions unless you know something I do not.
http://krebsonsecurity.com/wp-content/uploads/2013/04/mafisayshehasgrum.png
lolz rip mafi he don’t have “Grum” bot src only me have it’s,mafi ripper lolz
jabber: smile@tsec.pro
What language is that? Ebonics? It’s not pig-latin.
I’ll have a go at a translation for you:
“Ha, poor old Mafi*, he doesn’t have the source code for the ‘Grum’ bot**, only I do. Mafi is trying to take credit from me, haha.”
see, it’s easy with a bit of guesswork 🙂
* presumably someone’s name
** software for sending out spam emails
This story is some serious “gangster $h1t”
I don’t understand how lurking is even possible if the forums are “exclusive”.
It’s like what Demonoid used to do before they were shut down. Starts out with a group of “trusted” members who in turn can hand out invite codes to other people. Then it multiplies like rabbits, quality control is out the window and everyone’s aunts and uncles are talking about it on Facebook. That’s why I don’t get how they’re weeding out members, how will they ever be fully “trusted” as the next thing? Paranoia be strong amongst them I bet.
I always wanted to try something like this but was always afraid of the risk with getting my machine(s) infected with malware. Years ago I spent some time playing around with the Nigerian scam lowlifes. Like what was already stated , you would need to do these kinds of things on a V.M. or a system using a version of Linux . Furthermore, you would also need to use some type of secure V.P.N. tunnel or proxy.
I now deal mainly with disabling /termination of phishing scams which is safe enough for me.
I understand what you’re trying to demonstrate but using Demonoid as an example is perhaps not the best one you could’ve chosen given that it was open to the public for a few days each and every month :p
There are many ways. You build up a pseudo identity, and then use that entity to build up the history and reputation of other entities that soon become trusted in certain communities. Another, more potentially fraught with legal complications, involves simply jacking an active account, usually because of lax security on the part of the authorized forum user or the forum itself (or both). There are other ways, but these are probably the most common.
Wouldn’t it make some sense to go all the way and publish your results under a pseudo identity?
That is, to avoid the sort of things “careful out there !” warns about.
Brian,
I’ve often wondered how law enforcement differentiates investigators and journalists (such as yourself) from actual ‘cybercriminals’ if and when they seize or take over these boards (or arrest a lot of people on them). I assume at a minimum you’ve been investigated just in the course of their business (maybe on csu or darkmarket years ago).
How often have you (or other people you know) been investigated for crimes while doing research? And how did you deal with it when/if it happened? Any funny stories? I would enjoy an article on this subject.
Somewhat related: I’ve seen a lot of people here in these comments (and related, in Xylitol’s related articles) talk about wanting to dabble in such things, and I wonder if they realise it is dangerous and tricky for them who do not have large blogging sites to prove a pure intent. It is one thing to toy with a Nigerian in a victim context and another to run around pretending to be “cybercriminals”. Isn’t it dangerous?
You have a lot to learn Katherine. It’s a game of patience and constant attention to details. If you’ve never done it, go to some game chat forums and start there.
hehehehe game forums. bring your best suit of armor as the flaming wars will pummel you senseless. be quit witted, know when to laugh and when to give up.
yeah… Talk about seasoning some one. I used to run gaming forums, its a tough “learning” environment . = Þ
There are a TON of ways to get into these so-called forums. If she has to throw a comment out like that, she is either clueless on how to do alternate methods or is looking for an easy, cheap and untrackable way to do this as a temp hobby until something else grabs her attention. Just my 2cents worth =P
Could be jealousy too. who knows. = X
I don’t believe ‘sp3cialist’ in that screenshot could be so careless as to give away his exact location. That has to be a spoofed location, surely.
It’s a one of many weird (and well known) finds imaged by Google Earth. If you plug those long/lat coordinates into Google Maps, and then zoom in, you can see it’s a picture of a fighter plane tucked inside what looks to be a city parking lot in France.
See: https://maps.google.com/maps?q=48.825183,+2.1985795&hl=en&sll=38.003385,-79.420925&sspn=4.258751,9.18457&t=h&z=16
Amazing. I won’t ask how it got there but that’s a very conveniently-placed road I can see. Long and absolutely straight.
Intriguing that the co-ordinates given are those of not of the plane but of something on the ground about 20 or 30 feet to the right of the plane. Whatever it is is surrounded neatly by the white rectangle that those co-ordinates define. ‘sp3cialist’ clearly finds it intriguing too. And I am in a way relieved to see that his given location – so precise – was intended to direct the curious to this bizarre piece of surrealism. Perhaps he has a sense of humour.
20 seconds on Google shows it’s a university in Paris where they study aeronautics. Not that weird then to have an old plane on display:
https://lh6.googleusercontent.com/-VKFSpeXcIA8/T8Zapyej7uI/AAAAAABAK6o/W9Z6l20ju4U/s1047/IUT+de+Ville+d%27+Avray
I’m pretty sure it’s a Mirage III
(http://en.wikipedia.org/wiki/Dassault_Mirage_III)
That is most definitely my fighter plane, why you want one?
Yes, why not? The perfect transport for a newly-rich businessman. Flashy, loud, and very, very fast. Guaranteed to get you noticed.
One word of advice. I am sure there are many in here that are actively searching for clues on what, where and how Brian uses in order to successfully infiltrate some of these organizations.
They gather data. if they have a general idea of where you live, they can gather generic IP address ranges. If they know your on a COX ISP, that just made their work alot easier.
I’d also change locations if you do this outside the home. If using a local open and free internet connection, and it can be identified by the bad guys, they can easily figure out when you sit down for your first sip of java in the AM and say howdy in person.
I don’t trust anonymizers, proxies and other setups that I have no control over. Sure you can run on a spoofed IP address and think your safe, but that changes your IP. make sure all the information cahnges, including your computer name and MAC adress so if cannot be tracked back.
Combine in the fact if they know exactly what setup you use, they can easily combine this information and much more. They can then use webserver logs and get a general idea when and where the visits happen.
I’ve been in the security field for a long, long time. What I am trying to say is don’t always rely on the same method working time and time again. All it takes is one piece of the puzzle at a time and they ( potentially the real bad ones) get their fill of their world becoming undermined. I hope nothing ever comes of threats, but remember – always keep your guard up.
I suggest never show your cards, and change them often. I suggest if people want to learn more about how to do anything, they visit amazon or other bookstores and read up on what they intend to do. Its great to give them a shiny object, but unless they know how to utilize it, make it random and untraceable its a sitting duck.
I am not paranoid, but think of the consequences – if you get roughed up by some international thugs for cracking a few of their eggs, the rest of the young and upcoming investigators will take a step back and wonder how to proceed.
Just be careful out there young man. I personally want to see many more posts, but not at the cost of your quality of life.
“Mafi’s watermarking system can extract the user ID used to take any screen grab”
One can take a picture of the screen with a half-decent camera and the screen’s owner will never know.
No George, that would not defeat this watermarking system. The components of it are not image-based; they are numbers-based, and the numbers needed to compute the result are there whether you take a screen shot or a picture of it with your mobile or point-and-shoot.
I guess I misunderstood the problem.
That is only if you include the watermark in the image though, right? If you do a screengrab that has been clipped to remove that portion of the page it shouldn’t be as easy to track, unless it is somehow embedded across the whole page in a non obvious way – which should still get screwed up by converting or altering the image most of the time, right?
Yes, which is I why I stated in the story that you could avoid the watermarking altogether by simply taking a screenshot without including the information in the sidebar, or by blocking it out.
From the story:
“Mafi’s watermarking system can extract the user ID used to take any screen grab as long as that image includes the information under the “Author” sidebar on the left edge of the forum page:”
For the record, you can see that I did exactly this in the screen shot I used for the Plesk 0day story
http://krebsonsecurity.com/wp-content/uploads/2012/07/plesk0day.png
…which is what prompted one of the DK admins (Fubar) to ask who’d spilled the beans about the watermarking system. I’m glad he noticed too, because that was intentional. I wanted them to know I’d figured out their system.
http://krebsonsecurity.com/wp-content/uploads/2013/04/teardropddoskrebsonsecurity.png
So did you finally find the location of my webcam & my dirty secrets? You know you want this sexy ass 🙂
some watermarks – especially corporate ones are positioned in the picture itself. Its code, so if some one attempts to copy or “steal” your pictures, brand or otherwise, its in the picture.
So, the crook sets up a forum like post – but it could be just a picture instead of an actual post. You do your screen capture. The people with the corporate watermark software can either delete it, or if it is reposted, find out exactly where copies of this image are.
Now how reliable a camera shot will be, and whether it distorts the image is questionable.
Its sort of like Steganography, where you can imbed something in a photograph. Steganography can be used for good and evil purposes – lets just hope they do not have any bad stuff that antivirus software cannot detect.
Corporate watermarking has been around for a long time. I am sure a simple google search will show you its capabilities. Remember these guys are crooks, and anything that is software related probably can be cracked by them in no time, getting the full benefit of registered software.
Well that is why I asked, most of the watermarks are pretty obvious but some like forum posts could be an interesting way to track activity… Just seems like the non-related stuff would be clipped out by habit but maybe not or it wouldn’t have come up.
When you get into alpha/transparent images it might be possible to embed something that isn’t obvious without the right kind of editor?
There are so many ways to track activity that it should really be assumed anything and everything on there is suspect. Great work though, very interesting to read about and follow.
Oh, and for those that don’t realize it, many of the software forums have the ability built in to track IP addresses as well. There are plug ins for all types of uses. Should one wander on one of these sites, do so with utmost care. Logging in as a regular user vice with full admin rights MAY save you, but honestly, with the sophistication and code that’s available to the crackers, coders and evil empires, I think no computer is safe from infection. Most of the newer malware can detect whether it is in a VM environment, so be careful in there !
Bad guys dont like it when you piss on them.
Keep drinking, keep leaking, make it rain Krebs.
The key to successful watermarks is geometry.
That’s actually good thinking. Mine would have been a discoloration that was made to look like the site theme or the other member’s choice, however it was slightly tweaked by server to imply an identity. Barely visible to the naked eye.
Thinking in terms of geometry gives so many more possibilities. Especially if you think in terms of ads, tables, decorative images, etc. Slight differences encode the number that represents each person. Excess whitespace might even be used. The number to encode can be pretty small as even a million users can be encoded in a few bytes of data.
Thanks. Been using it (and other techniques like it) for years… Somewhere :).
One of the more interesting attributes of such a system is it also enables you to find out if you’ve been hacked, not just exposed via a user account.
Stay tuned for my kickstarter! Oh but am not American resident, well darn it.
I should clarify: Nowhere where the user who might hack it might know to look for it at.
I won’t say how publicly for obvious reasons. I’d appreciate your not exploring it in comments either. Just bored so thought I’d get you thinking Nick. 🙂
So Brian… I find your blog to be one of the few I bother to checkup on because you usually have interesting stuff. I’m curious… are you just looking the other way for the people who handed you this information? Considering the parties involved in the compromise are much dirtier than you expect. A small piece of information, after xylit0l’s post, the servers behind darkode were for unknown reasons hit with > 1gbit of ddos April 1st, then April 2-3rd around 800 mbit of ddos. Finally they gave up when they realized the new server is virtually impervious to a ddos attack. Care to comment?
And a message to the baboons behind the ddos, I dare you to try and known the new server offline.
*bets $1,000 you aint got the juice*
Looks like there may be an imposter then, since the real “sp3cial1st” seems to hit live-forums.com, naijafinder, hackforums,9dat and blackhatgroup to name a few.
Its basically the same ole’ boring posts, with little to know replies. They must be catching on to the real “sp3cial1st” crappy reputation.
“sp3cial1st” even appears to have an account on the Battlefield series, but that is probably ome lamer using this stereotypical name that many can come up with.
I bet you money it’s the same person in most of the cases. especially the one in regards to HF, etc
sp3cial1st – if you think ddos-guard.net is your “impervious” to ddos provider, you’re as stupid as they’re making you out to be everywhere. You obviously have no idea what you’re talking about at all.
Do you even understand what the internet is? A network of networks – right? You’re on the INTERnet. The only way I see a server anywhere being “impervious” is being on a closed INTRAnet but even then, flipping the electricity would deny you of service – correct? You claim to be a coder but your logic is by far, less than up to par.
You talk a lot of garbage. Just because you can install a bulletin board, run your mouth for years on other BBS, beg for information and eventually start one of your own and begin to dabble in coding but mainly know of coders (who aren’t that talented to begin with as they’re just taking and packaging publicly available POC and selling it as a kit. Or they may purchase some “0day” at the time from a talented reverse engineer until he sees he’s gotten as much money as he can out of you morons and then submits it to seclists etc and it’s patched.), doesn’t make you who you think you are. You all talk a lot of trash until the time someone notices you and takes a little time to find out exactly who you are because most of the time it’s not that difficult. People like you have an inflated sense of self-worth, self-importance and pride that is quite funny to read about. How you present yourself as some kind of “criminal” mafioso who can “call shots”.
In real life you’re either an over-weight mama’s boy, a hermit type geek with low self-esteem and no sense of personal hygiene or just some idiotic chap who knows a little and thinks he knows it all.
I’ll look for the news post with your nickname on it soon.
1. You are all talk and no beef. If you think the server isn’t impervious prove me wrong. Otherwise kindly go fc.k yourself.
2. You do realize there is a 0day for sale on darkode right now? Well two actually 🙂
3. I’m not a body-builder but not hard on the eyes either. Oh yea… I have an addiction to sex, for some-reason I can’t live without it every 10-12 hours. Let me know when you see me in the news at the playboy mansion boss.
I would not call dukie plumbing a man sex but some people do.
I didn’t know null routing an IP would still allow your members to access it still? There is your “impervious” server, moron.
How about add me on jabber and do something other than rant like a whiny bitch on brains blog? Oh wait… you’re a coward.
that’s pretty rich, specialist, you calling commenters here on the forum ‘cowards’ when you are admin of crime forum where everyone hides behind nicknames while stealing other peoples’ money and resources.
i think we know who real coward here is. go back to your little forum and leave the analysis to the big boys.
What is BS meter?
BS meter = bullshit meter
What Krebs meant to say is that normally he is highly suspicious of everything — unless he is able to independently confirm the datum/data — but that in this particular instance that that he wasn’t suspicious enough.
sp3cial1st
Your 2. comment only adds substantial proof as to what I’ve told you but you’re obviously to simple minded to think that is something to brag about – which it’s not.
As for 1. you’re obviously blind to the obvious, I’m not on your side. Also those taunts only show me who is the true “coward” as you’d like to put it. You’re a typical person in the trade you’re in. This is your way of having a sense of importance without doing much at all but running YOUR mouth.
I’d like to comment on you being so kind as to grace us with your presence and comment on “brains” blog as you put it. Kinda funny how someone would be bothered so much by a blogger. He’s not your typical blogger, writer or whatever you want to label it as – shoot look at his track record, look at the proof he’s already posted of your consistent attempts to disrupt his work or otherwise cause him grief and things of that nature. He must be doing what he does very well. I mean, coming from you – you’re untouchable right? You sure to vent off a lot of hot steam.
I honestly see you, your board and its members upsetting a scene you honestly shouldn’t have attracted at all. Like I said, your kind only lasts as long as certain groups allow you to. That’s only because they haven’t caught wind of you (you pissing the wrong people off), aren’t bored enough or you’re just not that big of a threat. Laugh all you want but the reality of things are it’s honestly only a matter of time now because you’ve attracted the wrong attention.
I meant nothing by what I said Mr Krebs either, please don’t take it the wrong way.
You make me laugh. I see now you are not only a coward but incompetent and fairly confused. You aren’t worth the time and effort to write a proper reply to so I’ll keep it short.
Yes you are right “I sit and run my mouth while doing nothing, and I’m invincible.” To a person involved in the scene, it is evident you have no idea what you are talking about.
You lack the ability to backup your statements, otherwise do something, … oh wait you can’t. Least we forget you prefer to sit here where you feel safe instead of having a chat with me.