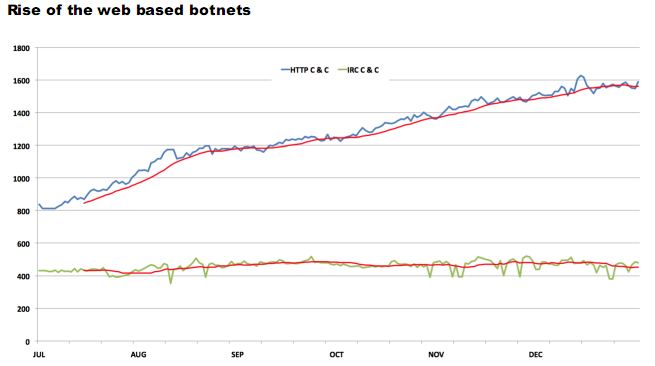
 The graphic above is from a report out today by Team Cymru, a group that monitors studies online attacks and other badness in the underground economy. It suggests an increasing divergence in the way criminals are managing botnets, those large amalgamations of hacked PCs that are used for everything from snarfing up passwords to relaying spam and anonymizing traffic for the bad guys, to knocking the targeted host or Web site offline.
The graphic above is from a report out today by Team Cymru, a group that monitors studies online attacks and other badness in the underground economy. It suggests an increasing divergence in the way criminals are managing botnets, those large amalgamations of hacked PCs that are used for everything from snarfing up passwords to relaying spam and anonymizing traffic for the bad guys, to knocking the targeted host or Web site offline.
The bottom line in the graphic shows the prevalence of botnets that are managed using Internet relay chat (IRC) control channels (think really basic text-based instant message communications). The blue line trending upward depicts the number of Web-based botnets, those that the botmaster can control with point-and-click ease using a regular Web browser.
According to Team Cymru, the number of Web-based botnets has continued to climb, doubling in number over the last six months. “This trend could be explained by the low cost of entry into the HTTP based botnet field: the kits are becoming more accessible and the easier user interface for HTTP botnets means that they are generally favored over more traditional control mechanisms.”
Read more of the Team Cymru report here (.PDF).
Last month, I profiled Virtest and AV-Check, a couple of services being marketed to malware writers who want to quickly scan their creations to see how widely they are detected by commercial anti-virus tools. The graphic above is another great example of the democratization of espionage, and what I’ve called Web Fraud 2.0: Web-based services and tools that make it simple for virtually anyone to profit from online crime.
Here are a few examples of Web Fraud 2.0 I’ve written about:
Franchising Cybercrime
Data Search Tools for ID Thieves
Faking Your Internet Address
Thwarting Anti-Spam Defenses
Distributing Your Malware
Digital Forgeries
Validating Your Stolen Goods
Cloaking Connections



People always applaud ease of use. 😉
This reminds me of what used to be called a “script kiddie”. Essentially a toolset that allows someone that isn’t that technically sophisticated to break into a computer.
Years and years ago I had a machine broken into. This was in the days before consumer firewall boxes were available -you used to need to set up a dedicated machine to work as a firewall.
In my case I had a Linux box connected directly to a cable modem. One morning I got a call from the ISP asking me to check things out – they had complaints from a 3rd party that my machine was attempting breakins, and that they noted what appeared to be a backdoor in my machine. It didn’t take long for me to confirm their findings. I started to try and undo the damage and then got a message on my console from the bad guys taunting me – I just shut down that machine right then and there so I could go to work.
Later I brought the thing back up without the network being connected, and used RedHat tools to identify which binaries were compromised. It was pretty amazing the lengths they would go to hide their tracks. They had replaced many of the normal tools that one would use to monitor the machine, and these would hide the evidence of their intrusions (backdoors, etc).
I bring this up as a counterpoint to those that assume that if they are running Mac or Linux that they are completely safe. You are only safe if the bad guys aren’t targeting your machine.
The best basic thing I ever read about security is from a sticky in the Security Forum at Ubuntu Forums:
(abridged)
“Introduction : Security is an ongoing process and, like an onion, it has layers and stinks. The best defense you have is to read and learn how to secure your OS.
Alas, there is no single action you can take to achieve absolute security (the only safe computer is one that is turned off, disconnected from the Internet, and in a locked vault) and security concerns and “ease of use” are sometimes competing concerns.
Summary: There is no such thing as “security in a box ™”. Information security is an active job — it is not installing some product on the system and sitting back and relaxing.”
http://ubuntuforums.org/showthread.php?t=510812
Exactly, computer security is an ongoing process. Not a set it and forget it type of thing. AV/malware software is NOT a panacea! The most important part of that process is the user behind the keyboard! It’s kept me safe 14+ years (even using the dreaded Windows + IE! ;P). A computer is NOT an appliance to be used like a toaster! It reminds me of a line in Spiderman, “With great power, comes great responsibility!” Botnets wouldn’t have a great majority of their spawn if people took responsibility for the power their computers wield! Most only have themselves to blame for becoming a botnet victim!
Don’t fall into the AV/anti-malware trap. Those tools are only good for performing Keystone Kops types of security – when the bad guys are already inside the perimeter. Concentrate instead on making sure you have multiple barriers and not just a by definition flaky defence at the perimeter.
Brian,
Some interesting data here. The trend of the graph is eye opening. Is there a version of the graph that goes back 12 or 18 months?
does the graph really indicate that HTTP is outpacing
IRC as the human (being generous in use of the term
here) operator’s C&C protocol or that the bots coordi-
nate their botwork using HTTP, because of the broad
acceptance of the Firewall Enhancement Protocol
http://www.faqs.org/rfcs/rfc3093.html
?
[note the publication date on that one, if you’re not
familiar with this “protocol” and its widespread (ab-)
use as the transport protocol for just about every high-
er (or lower [grin]) layer protocol implemented lately
that moves just about any data around that’s not email
or BitTorrent, so, yes, i suppose it’s natural it’s moving
people’s credit card numbers and personally identify-
ing information around, too, and bot C&C. my only
question, in that case, is do the bad guys use XMLRPC,
SOAP, JSON, REST, or what?]
the franchising business is actually good specially if the product for franchise is well known.*-*
Franchising business is good but some franchise needs some cold hard capital to start with.~~~